Introduction:
In today’s interconnected world, where information flows seamlessly between devices and across continents, understanding network topology is crucial. Network topology refers to the arrangement of devices, connections, and communication paths that make up a computer network. Just like roads and highways determine the flow of traffic, network topology defines how data travels within a network. In this blog post, we will explore the basics of network topology, delve into different types of topologies, and discover why learning about it is essential, even for hackers.
What is Network Topology?
Network topology encompasses the physical and logical layout of a computer network. It outlines the connections between devices and the data transmission between them. Just as a blueprint outlines the structure of a building, network topology outlines the structure of a network.
Different Types of Network Topologies
-
Bus Topology:
Imagine a long, straight road with houses on both sides. In a bus topology, devices are connected to a single cable called a bus. This type of topology is simple and inexpensive, but if the main cable fails, the entire network can go down.
-
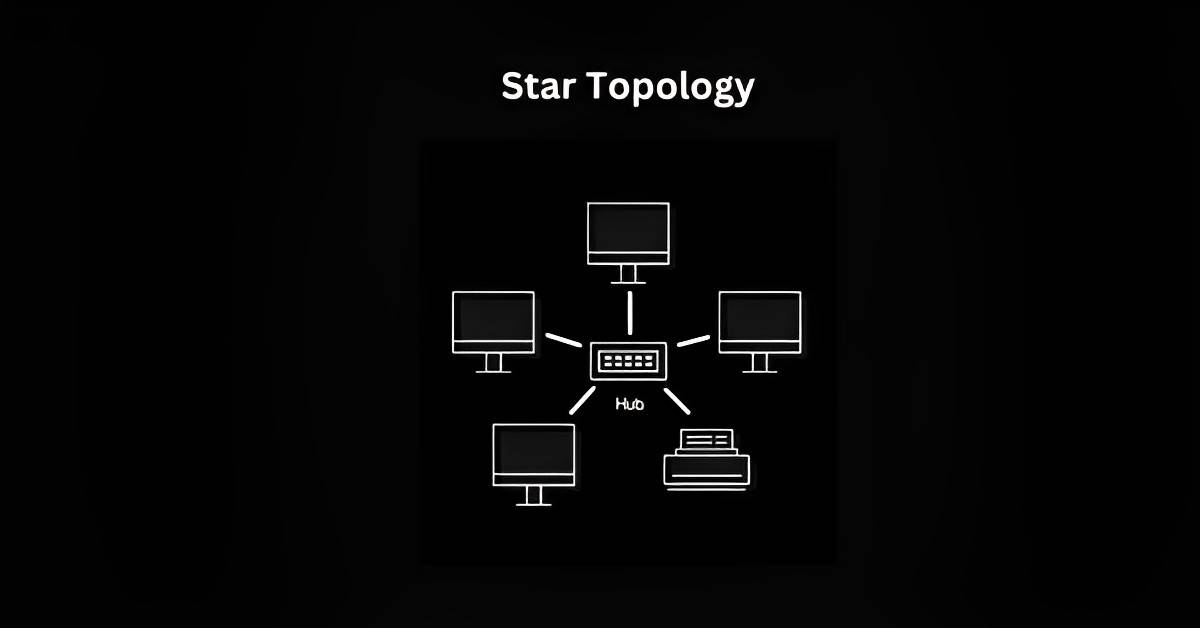
Star Topology:
Picture a central hub with multiple roads leading to different houses. In a star topology, devices connect to a central device, such as a switch or router. If one device fails, it doesn’t affect the rest of the network, making it reliable. However, it heavily relies on the central device, which, if it fails, can disrupt the entire network.
-
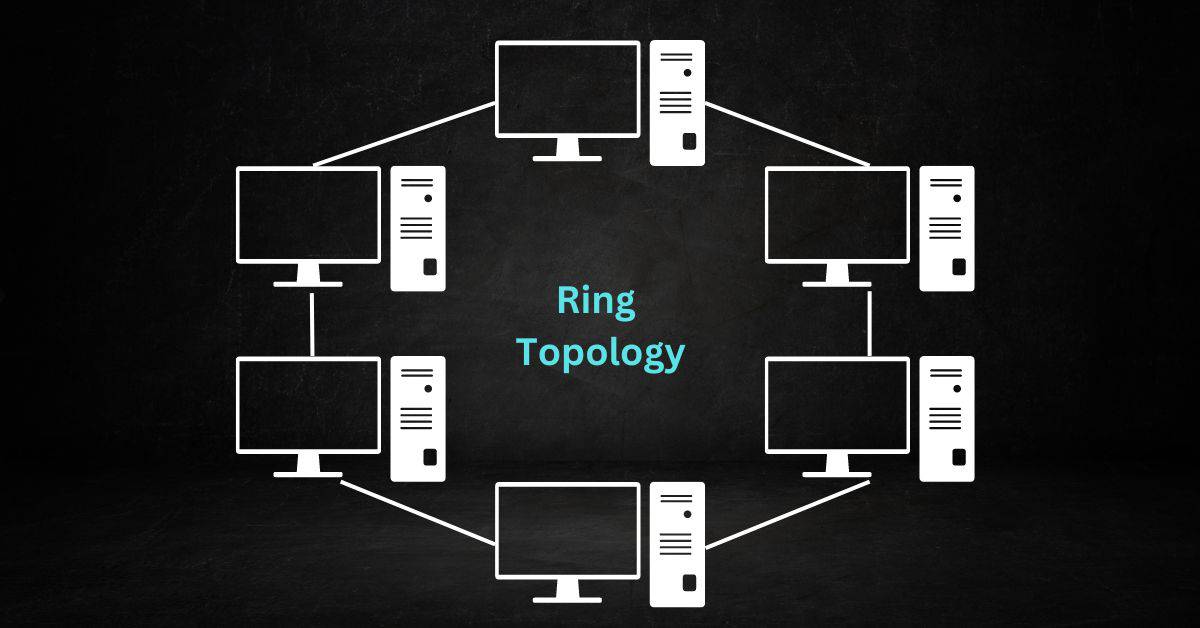
Ring Topology:
Visualize a circular road where each house is connected to its neighboring houses. In a ring topology, devices form a closed loop. Data travels in one direction, passing through each device until it reaches the intended destination. While it offers equal access to all devices, a single break in the ring can disrupt the entire network.
-
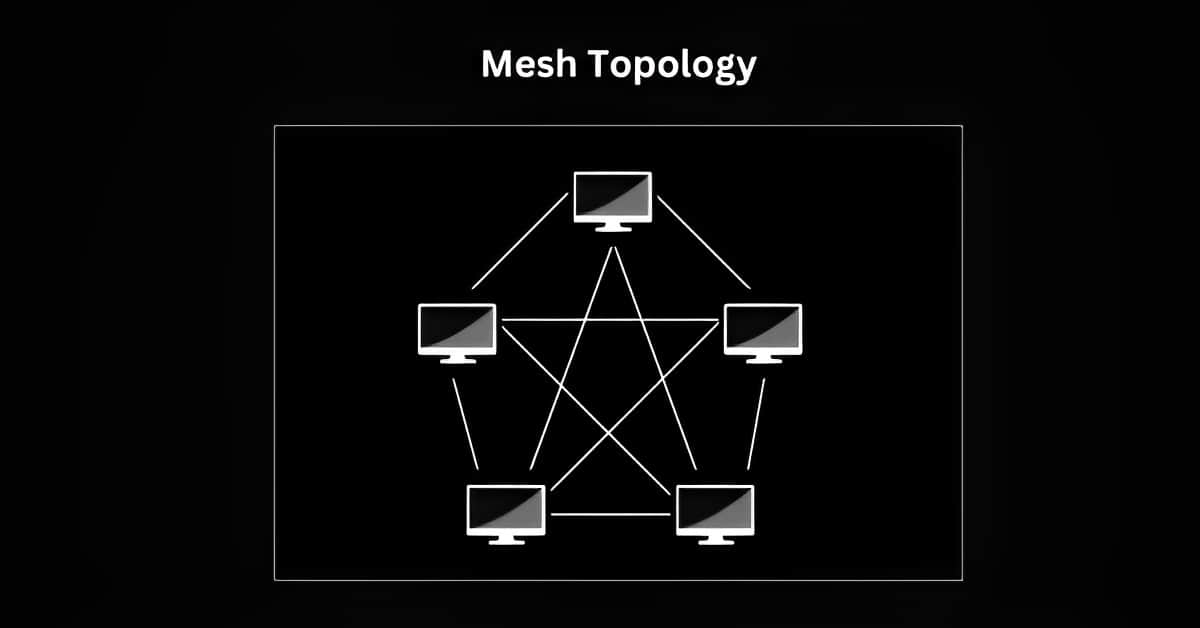
Mesh Topology:
Imagine a complex road network where every house has direct connections to multiple other houses. In a mesh topology, each device is connected to every other device, creating redundant paths. This redundancy ensures high reliability and fault tolerance, but it can be costly and complex to implement.
-
Hybrid Topology:
A hybrid topology combines different types of network layouts, like connecting houses with roads. It’s like having multiple ways to reach other houses. This helps make sure everyone stays connected even if some paths are blocked. It’s a smart and flexible way to build networks, just like a complex road system with different routes.
-
Double Ring Topology:
Imagine two interconnected rings, like two circular paths. In a double ring topology, data travels on both paths. It’s like having a backup plan in case one path gets blocked. This makes sure communication keeps going, even if there’s a problem in one of the rings. It’s a reliable and safe way to set up networks, just like having two roads to reach a destination.
Why is Learning Network Topology Important for Hackers?
Network topology plays a crucial role in the world of hacking and cybersecurity. Here’s why hackers find it essential to understand network topology:
-
Identifying Vulnerabilities:
By studying network topology, hackers can identify potential weak points or vulnerabilities within a network. Understanding how devices are connected and data flows enable8opip- hackers to pinpoint areas that can be exploited.
-
Planning Attack Routes:
Knowledge of network topology allows hackers to plan their attack routes strategically. By identifying critical devices, entry points, and paths with the least security, they can optimize their efforts to gain unauthorized access.
-
Exploiting Network Weaknesses:
In-depth knowledge of network topology empowers hackers to exploit specific weaknesses efficiently. By understanding the network’s structure, they can exploit misconfigurations, outdated software, or weak security measures.
-
Covering Tracks:
Hackers who grasp network topology can navigate through a network while leaving minimal traces. By understanding the paths data takes and the devices it encounters, they can erase their digital footprints and remain undetected for longer periods.
You may also like:
https://hackedyou.org/10-important-browser-cookies/
https://hackedyou.org/everything-about-internet-cookies/
https://hackedyou.org/network-protocols-types-and-uses/
https://hackedyou.org/hackers-exploiting-open-ports/
https://hackedyou.org/client-server-model/
https://hackedyou.org/ip-addresses-basics-explained/
https://hackedyou.org/top-20-networking-fundamentals-for-hackers/
https://hackedyou.org/artificial-intelligence-transforming-cybersecurity/
https://hackedyou.org/top-10-major-cybersecurity-threats-in-2023/