Introduction:
Networking is crucial for hackers as it allows them to exploit vulnerabilities in connected systems. By understanding the intricate network of devices, protocols, and connections, hackers gain valuable insights into potential entry points for attacks. Mastering networking empowers hackers to navigate complex networks, identify weaknesses, and launch targeted hacks. In this blog, I will provide a basic overview of networking fundamentals, covering key points. Please note that this blog is just an introduction, and I will explore each aspect in more detail in future posts. So, stay tuned for more in-depth discussions on networking and its significance in the world of hacking.
-
IP address:
An IP (Internet Protocol) address is a special numerical identifier given to each device connected to a network. Hackers frequently take advantage of weaknesses in IP addresses to infiltrate targeted systems or conceal their identity. It is essential for hackers to comprehend IP addressing and the related protocols in order to navigate networks effectively. Understanding these concepts allows hackers to traverse network structures with ease.
-
Subnetting and CIDR:
Subnetting and CIDR (Classless Inter-Domain Routing) are important things to know about networks. Subnetting is like dividing a big neighborhood into smaller blocks. It helps hackers find specific targets within a network and plan their attacks better.CIDR is like a special tool that helps give out addresses in a smart way and defines the boundaries of those blocks. It helps hackers understand how networks are organized and make their hacking plans even better.
-
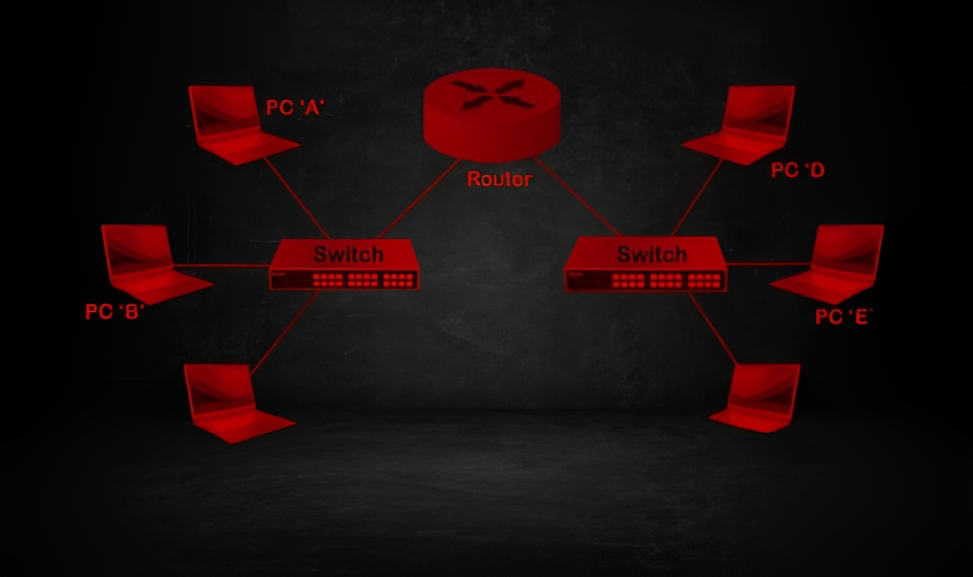
Routers and Switches:
Routing and switching are fundamental aspects of network communication. Routing and switching are like the traffic directors of computer networks. They help make sure information gets to the right place. Routers are like GPS systems that guide data packets between different networks. They make sure the information goes to the right destination. Switches are like connectors that help devices within the same network talk to each other. They make it easy for devices to exchange information. For hackers, understanding routing and switching is important because it helps them understand how data moves around in a network. They can learn how to analyze and even change the flow of information.
-
Ports and Protocols:
In a network, ports serve as virtual endpoints that enable different applications or services to communicate with one another. Each port is associated with a specific protocol, like HTTP (port 80) for web traffic or FTP (port 21) for file transfers. However, it’s important to be aware that open ports and vulnerable protocols can be exploited by hackers to gain unauthorized access or launch attacks on a network. By gaining knowledge about ports and protocols, hackers can effectively navigate and manipulate network communications, thereby identifying possible vulnerabilities and strengthening network security.
-
Firewalls:
Firewalls play a vital role in network security by filtering both incoming and outgoing network traffic, acting as a protective barrier. They help keep the network safe from unauthorized access. Understanding how firewalls are set up and identifying their potential weaknesses is crucial for hackers. This knowledge allows them to explore ways to bypass or exploit the firewall’s defenses in order to gain unauthorized access. By learning about firewalls, hackers can enhance their skills and knowledge, enabling them to overcome network security measures.
-
Network Scanning:
Network scanning is a way for experts to explore and understand computer networks. Hackers use this technique to find weak spots and learn about the network’s secrets. They use special tools like Nmap, Nessus, or OpenVAS to help them in their work. For hackers, understanding network scanning is important because it allows them to gather important information about a network. They can find out which devices are active, discover open doors (called ports), and see what services are running. By knowing these things, hackers can find places where they might be able to get in and do things they shouldn’t.
-
VLANs and VPNs:
VPNs (Virtual Private Networks) are like secret tunnels that help protect your information when you use the internet, especially on public Wi-Fi networks. They keep your identity safe and make it difficult for others to know where you are. But remember, VPNs are not just for bad people. Regular people and companies use them too, to securely access their work information from home and keep their personal stuff private. Now, imagine a big playground divided into smaller sections. That’s what VLANs (Virtual Local Area Networks) do for computer networks. They split a big network into smaller parts, so information can stay separate and safe. Bad people might want to know about VLANs and VPNs to hide what they’re doing or bypass network rules. But it’s important to always use this knowledge responsibly and not for doing anything harmful.
-
Network Address Translation:
Network Address Translation (NAT) is like a translator for IP addresses. It helps devices in a private network talk to the outside world using a single public address. Imagine you have many people in your house, and you all want to talk to someone who is outside your house. NAT helps you all use the same phone number to call, so it looks like you’re all coming from the same place. For hackers, understanding NAT is important because it helps them find ways to get around network restrictions. They want to learn how NAT works, how to change the rules, and even how to go through it without being noticed.
-
Virtualization and Cloud Networking:
Virtualization and cloud networking are like special technologies that have changed how networks work. Hackers should learn about these technologies and understand concepts like virtual networking, virtual switches, and software-defined networking. Imagine you have a magical box that can create many smaller worlds inside it. Each world has its own rules and devices. Hackers need to understand how these smaller worlds connect to each other and how they can find weaknesses in them. In virtualized and cloud environments, hackers can find mistakes or problems that are different from traditional networks. By understanding how these special networks are set up and secured, hackers can take advantage of any mistakes or problems they find.
-
Network Access Control (NAC):
Network Access Control (NAC) is like a special security guard for a network. It checks and controls the devices that want to connect to the network. Imagine you have a secret club, and there’s a guard at the entrance. Before anyone can come inside, they have to show their special membership card and follow certain rules. NAC does the same thing for networks. For hackers, understanding NAC is important because they want to find ways to get around this security guard. They want to learn how NAC works, how to trick it, or even find mistakes in its rules to get inside without permission.
-
(IDS/IPS):
Intrusion Detection and Prevention Systems (IDS/IPS) are like special guardians for a network. They watch over all the traffic and look for any bad or dangerous activities. Imagine you have a team of superheroes that can see and stop villains trying to harm your city. IDS/IPS are like these superheroes for networks. They keep a close eye on all the network traffic to catch any bad guys or harmful actions. For hackers, it’s important to know about IDS/IPS because they want to find ways to avoid being caught. They want to learn how to trick the superheroes, like using secret codes or changing their appearance, so they can carry out their attacks without being detected.
-
Network forensics:
Network forensics is like being a digital detective. It’s all about investigating and analyzing the data that travels through a network to solve mysteries and catch hackers. Imagine you’re a detective trying to solve a case. You gather clues and carefully study everything to figure out what happened. Network forensics is similar, but instead of a physical crime scene, we look at the data that moves around the network. For hackers, understanding network forensics is important because they want to cover their tracks and not get caught. They want to learn how investigators work, like looking at captured data, studying logs, and reconstructing events. This helps them hide what they’re doing or find weaknesses in the network’s security.
-
Wireless Security Protocols:
Wireless security protocols are like locks that keep our Wi-Fi networks safe. Similar to having a key to open your door, these protocols protect our wireless networks from unauthorized access. Different security protocols exist, including WEP, WPA, and WPA2. However, hackers need to be aware of these protocols’ vulnerabilities, just as certain locks may be simpler to pick than others. For example, WEP can be cracked easily, and WPA/WPA2 can be vulnerable to attacks that try different passwords until they find the right one. Hackers who want to exploit these weaknesses use special tools, like Aircrack-ng or Reaver, to test the security of wireless networks. They try to find networks with weak security settings and break into them.
-
Network monitoring:
Network monitoring is like being a vigilant observer, always keeping an eye on a bustling street. It involves using special tools to carefully watch over a network and ensure everything is running smoothly. Just as security cameras help spot any unusual activity in a neighborhood, network monitoring tools help us detect any irregularities or potential issues within a network. This could be anything from unusual network traffic patterns to performance bottlenecks. For hackers, understanding network monitoring is crucial because they want to find weaknesses or vulnerabilities in a network’s defenses. They want to know which areas are less secure and can be exploited for their activities. Tools like Nagios, Zabbix, or PRTG assist hackers in gathering valuable information about the network systems, enabling them to plan their actions more effectively.
-
Network segmentation:
Network segmentation is like dividing a big pizza into individual slices. Each slice is separate from the others, making it easier to control and protect. For hackers, understanding network segmentation is important because it allows them to identify specific areas within a network that may have weaknesses or vulnerabilities. Imagine if each slice of pizza represents a different part of the network, like departments in a company. Hackers can explore each segment separately to find potential entry points or vulnerabilities. By learning about techniques like VLANs (Virtual Local Area Networks), subnets, or network zoning, hackers can navigate through the segmented network and search for areas that may be easier to exploit. It’s like finding the weakest slice of pizza that can be easily taken.
-
Network load balancing:
Network load balancing is like having multiple cashiers in a store to make sure customers are served quickly and evenly. It helps distribute the workload and keeps everything running smoothly. For hackers, understanding network load balancing is important because it can reveal potential weaknesses or vulnerabilities. Imagine if each cashier represents a server or network device. Hackers can exploit the load balancing mechanisms or misconfigurations to disrupt services or gain unauthorized access to target systems. By learning about load-balancing algorithms and techniques, hackers can identify the best ways to manipulate the system and cause disruptions. It’s like finding a way to create chaos in the store by overwhelming the cashiers or taking advantage of their weaknesses.
-
Quality of Service (QoS):
Imagine you’re at a party where everyone is trying to talk at once. It can get chaotic and hard to understand each other. Quality of Service (QoS) is like having a system that helps organize and prioritize the conversations so that important messages are heard clearly. For hackers, understanding QoS is important because they can exploit its mechanisms and weaknesses. It’s like finding a way to manipulate the conversation and disrupt the flow. By learning about traffic shaping and bandwidth allocation techniques, hackers can identify vulnerabilities in the system and potentially disrupt services or gain unauthorized access. Think of it as someone who knows how to take advantage of the party’s organization to cause disruptions or sneak into restricted areas. Understanding QoS helps hackers figure out how to disrupt the flow of communication and potentially gain an advantage.
-
Network Authentication and Authorization:
Imagine you have a secret club where only members with the right password or access card can enter. Network authentication and authorization work in a similar way, but instead of a club, it’s about protecting valuable network resources. For hackers, understanding network authentication and authorization is important because it helps them find ways to bypass or exploit these security measures. It’s like figuring out how to sneak into the club without having the correct password or access card. By learning about authentication protocols like RADIUS or TACACS+, hackers can identify vulnerabilities in the system and potentially gain unauthorized access to network devices or services. Think of it as someone who knows how to trick the club’s security system to gain access to restricted areas. Understanding authentication bypass techniques or vulnerabilities in authentication systems helps hackers find loopholes in the system and potentially gain an advantage they shouldn’t have.
-
Network Redundancy and Failover:
Imagine you have two ways to connect to the internet at home: Wi-Fi and a mobile hotspot. Normally, you use Wi-Fi because it’s faster and more reliable. But if the Wi-Fi suddenly stops working, your devices automatically switch to the mobile hotspot to keep you connected. For hackers, understanding network redundancy and failover means they can try to exploit weaknesses in the backup connection. For example, they might try to disrupt the switch from the main connection to the backup connection, causing a temporary loss of internet. During this disruption, they could attempt unauthorized access or disrupt operations. So, network redundancy and failover are important for continuous internet connectivity. However, hackers can use these mechanisms as opportunities to cause disruptions or carry out unauthorized activities.
-
Network documentation and diagrams:
Network documentation and diagrams are like maps that provide important information about how a network is structured and connected. Just like a map helps you navigate and understand different places, network documentation, and diagrams help us understand how devices and systems are set up in a network. For hackers, having the ability to read and interpret network documentation is crucial. It allows them to understand the network’s layout, identify important devices, and plan their attacks more effectively. By studying the documentation, hackers can pinpoint the weak points in the network and devise strategies to exploit them. So, network documentation and diagrams are valuable resources for both network administrators and hackers. They provide insights into the network’s architecture and help hackers understand the network’s vulnerabilities, enabling them to plan targeted attacks more effectively.
If you found this blog helpful, make sure to check out my other informative posts on related topics to further enhance your understanding. Follow the links below to expand your knowledge: