What is the TCP/IP Protocol?
Imagine computers as superheroes with extraordinary powers, but they need a common language to communicate effectively. That’s precisely what the TCP/IP (Transmission Control Protocol/Internet Protocol) provides – a super language for computers to understand and interact with each other. Without the TCP/IP protocol, the internet, as we know it, wouldn’t exist!
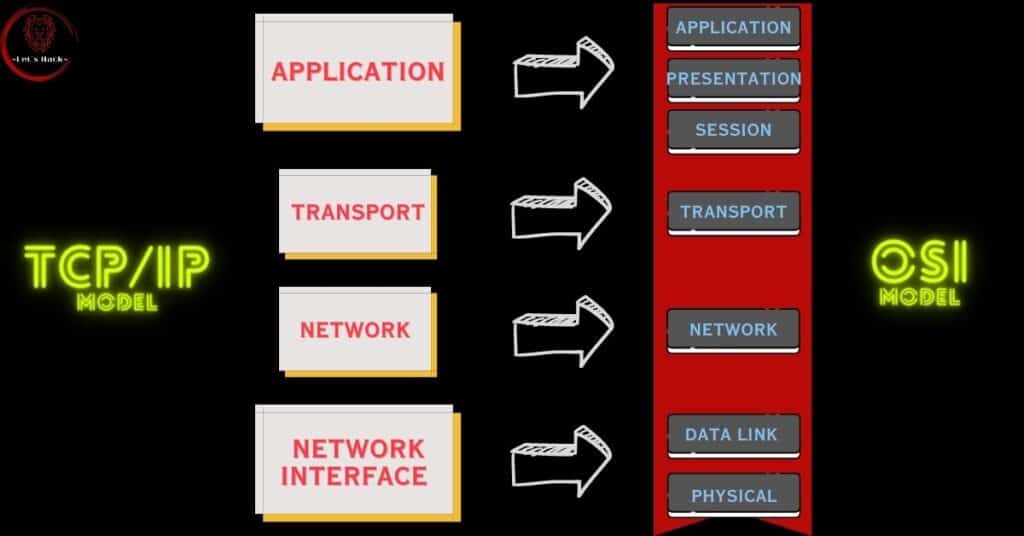
The TCP/IP Layers: Building Blocks for Digital Communication
To understand how the TCP/IP protocol works, let’s break it down into four essential layers, each with a special role to play:
-
The Application Layer: The Multitalented Players
At the topmost layer, we have applications that bring life to our digital world. Just like talented actors in a theater performance, applications like web browsers, email clients, and file transfer programs ensure that data is correctly packaged and ready for transmission.
-
The Transport Layer: The Reliable Messengers
Imagine you have a secret message you want to send to a friend, but it’s too long to fit in a single envelope. The Transport layer comes to the rescue! It divides your message into smaller parts called packets and numbers them, like puzzle pieces, to ensure they can be reassembled correctly. The most popular messenger at this layer is the Transmission Control Protocol (TCP), which makes sure that all the packets reach their destination safely and in the right order.
-
The Internet Layer: The Navigator
Have you ever used GPS to find the best route to a destination? Well, the Internet layer acts like a super-smart navigator for data packets. It assigns unique addresses called IP addresses to devices, just like giving each house on a street a specific number. These addresses help the packets find their way through various networks, crossing routers like traffic intersections until they reach their intended destination.
-
The Network Interface Layer: The Physical Connection
Now, let’s dive into the physical aspect of communication. The Network Interface layer handles the actual connection between your computer and the network. It’s like the highway on which data travels. This layer manages tasks such as converting data into electrical signals, managing network cables, and addressing hardware devices. One popular protocol used here is Ethernet, which allows devices to connect via wired or wireless networks.
Putting it all Together:
Imagine you want to send an email to your friend who lives far away. Let’s see how the TCP/IP protocol works in action:
-
Application Layer:
You compose your email using an email application like Gmail. The application neatly packages your message, adding important details like the sender, recipient, and subject.
In the Application Layer of the TCP/IP model, several protocols are used some commonly used protocols in the Application Layer include:
-
-
- HTTP (Hypertext Transfer Protocol): Used for transmitting web pages and data on the World Wide Web.
-
-
-
- FTP (File Transfer Protocol): Primarily used for transferring files between a client and a server.
-
-
-
- SMTP (Simple Mail Transfer Protocol): Responsible for sending and delivering email messages over the Internet.
-
-
-
- DNS (Domain Name System): Converts domain names (like www.example.com) into corresponding IP addresses.
-
-
-
- DHCP (Dynamic Host Configuration Protocol): Assigns IP addresses and network configuration information to devices on a network.
-
-
-
- SNMP (Simple Network Management Protocol): Enables the monitoring and management of network devices.
-
-
-
- POP (Post Office Protocol): Retrieves email from a remote server to a local client device.
-
-
-
- IMAP (Internet Message Access Protocol): Allows email clients to access and manage email messages stored on a server.
-
-
Transport Layer:
The TCP takes the email from the application layer and breaks it into smaller packets. It assigns a number to each packet, ensuring they are ready for their journey. TCP also acts as a diligent messenger, making sure all the packets arrive at the destination and in the correct order.
In the Transport Layer of the TCP/IP model, two primary protocols are commonly used:
-
-
- TCP (Transmission Control Protocol): This protocol provides reliable, connection-oriented communication. It ensures that data packets are delivered in the correct order and without errors. TCP establishes a connection between the sender and receiver, handles flow control, and retransmits lost or damaged packets if necessary. It is widely used for applications that require guaranteed data delivery, such as web browsing, file transfer, and email.
-
-
-
- UDP (User Datagram Protocol): Unlike TCP, UDP is a connectionless and unreliable protocol. It offers fast and lightweight communication by sending data packets, called datagrams, without establishing a connection or verifying delivery. UDP is commonly used for real-time applications such as video streaming, voice over IP (VoIP), online gaming, and DNS lookups, where speed and efficiency are more important than guaranteed delivery.
-
-
Internet(Network) Layer:
Here, the IP comes into play. It adds the IP addresses of your computer and your friend’s computer to each packet. Just like a magic GPS, IP guides the packets through different networks, helping them find the most efficient path to reach your friend.
In the Internet (Network) Layer of the TCP/IP model, the primary protocol used is:
-
-
- IP (Internet Protocol): The Internet Protocol is responsible for addressing and routing data packets across networks. It assigns unique IP addresses to devices connected to the internet, allowing them to identify and communicate with each other. IP determines the best path for data packets to reach their destination by working with routers, which act as traffic directors. IP provides a logical addressing system that enables global connectivity and seamless data transmission across different networks.
-
Additionally, there are supporting protocols used in the Internet Layer, including:
-
-
- ICMP (Internet Control Message Protocol): ICMP is used for network diagnostics and error reporting. It helps devices communicate status and error messages, such as when a destination host is unreachable or when a packet encounters an issue during transmission.
-
-
-
- ARP (Address Resolution Protocol): ARP maps IP addresses to physical MAC addresses on a local network. It helps devices identify and communicate with each other within the same network.
-
-
Network Interface Layer:
The packets are transformed into electrical signals and travel through your computer’s network card, across the internet, and eventually arrive at your friend’s computer.
When the packets reach your friend’s computer, the TCP/IP protocol works in reverse, assembling the packets and delivering your email to their email application.
In the Network Interface Layer of the TCP/IP model, various protocols and technologies are used to establish and maintain the physical connection between devices. Some commonly used protocols and technologies in the Network Interface Layer include:
-
-
- Ethernet: Ethernet is a widely used protocol for local area networks (LANs). It defines the rules for transmitting data over network cables, such as twisted-pair copper cables or fiber optic cables. Ethernet handles tasks like addressing devices on the network, managing data collisions, and providing reliable data transmission.
-
-
-
- Wi-Fi (Wireless Fidelity): Wi-Fi is a wireless networking technology that allows devices to connect to a network without the need for physical cables. It uses radio waves to transmit and receive data between devices and access points. Wi-Fi enables wireless connectivity in homes, offices, public spaces, and other areas with Wi-Fi coverage.
-
-
-
- MAC (Media Access Control) Addressing: MAC addresses are unique identifiers assigned to network interface cards (NICs) of devices. They are used to identify devices on a network at the hardware level. MAC addressing helps ensure that data is properly delivered to the intended device within a local network.
-
-
-
- PPP (Point-to-Point Protocol): PPP is a protocol used for establishing a direct connection between two devices over a serial link, such as telephone lines or leased lines. It provides authentication, error detection, and encapsulation of data for secure and reliable communication between devices.
-
-
-
- DSL (Digital Subscriber Line): DSL is a technology that allows high-speed internet access over traditional telephone lines. It enables simultaneous voice and data transmission, providing broadband connectivity for homes and businesses.
-
You may also like:
https://hackedyou.org/tcp-ip-vs-osi-model/
https://hackedyou.org/http-status-codes-explained-all/
https://hackedyou.org/what-is-a-cdn-and-how-does-it-work/
https://hackedyou.org/dns-resolver-explained/
https://hackedyou.org/understanding-network-topology/
https://hackedyou.org/10-important-browser-cookies/
https://hackedyou.org/everything-about-internet-cookies/
https://hackedyou.org/network-protocols-types-and-uses/
https://hackedyou.org/hackers-exploiting-open-ports/
https://hackedyou.org/client-server-model/
https://hackedyou.org/ip-addresses-basics-explained/
https://hackedyou.org/top-20-networking-fundamentals-for-hackers/
https://hackedyou.org/artificial-intelligence-transforming-cybersecurity/
https://hackedyou.org/top-10-major-cybersecurity-threats-in-2023/
https://hackedyou.org/mastering-cybersecurity-2023-ultimate-guide/