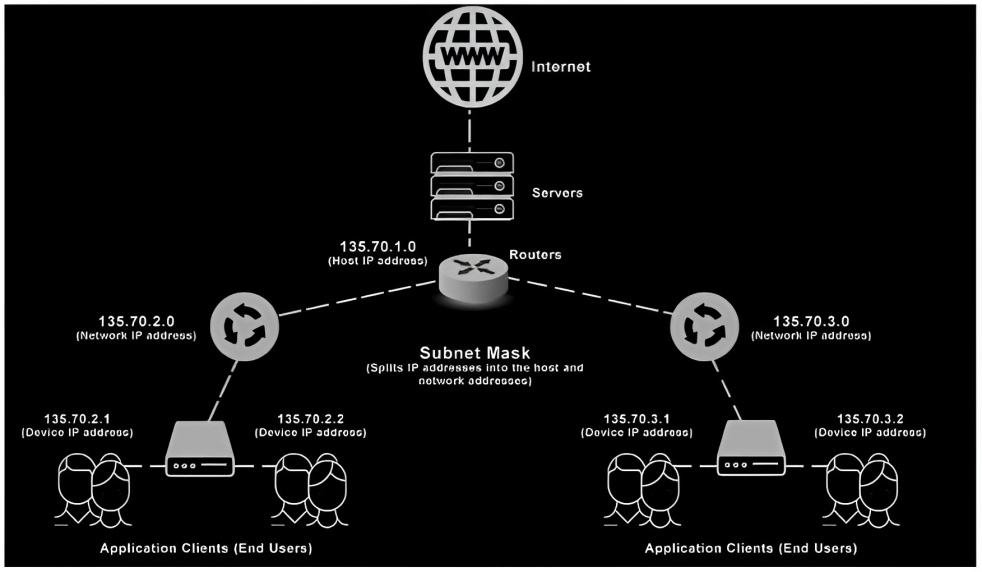
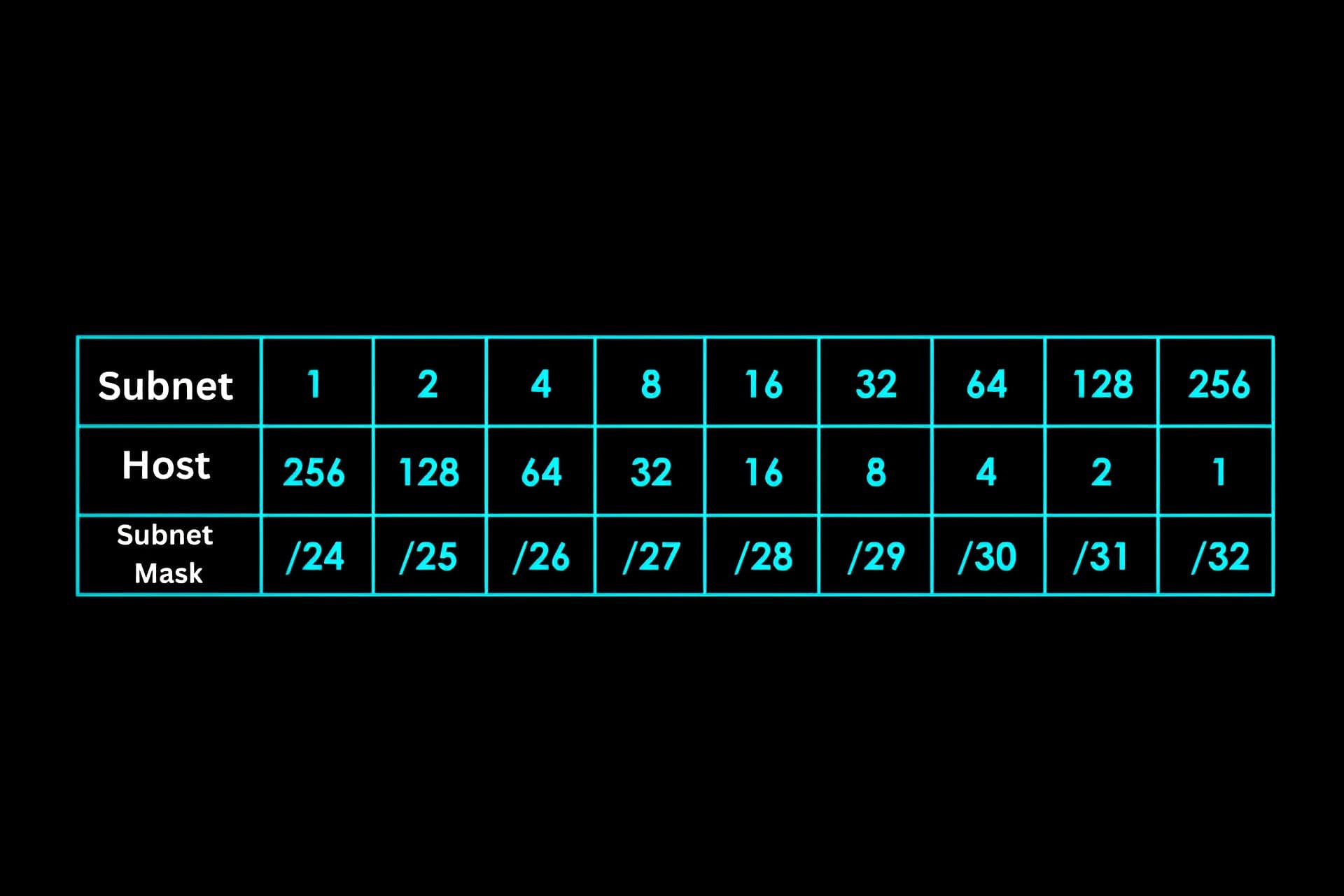
What is Subnetting?
Subnetting is like creating smaller neighborhoods within a big city. In computer networks, it involves dividing a large network into smaller, more manageable subnetworks or subnets. Each subnet acts like its own mini-network, allowing devices within it to communicate more efficiently.
Why Do We Need Subnetting?
Subnetting plays a vital role in computer networks for several important reasons that make our digital world run smoothly:
- Efficient Address Allocation: Just like planning a village layout, subnetting helps us allocate IP addresses more effectively. By dividing networks into smaller subnets, we optimize address usage and make the most of available resources.
- Boosted Network Performance: Imagine a busy highway with multiple lanes instead of a single road. Subnetting works similarly by dividing networks into smaller segments, spreading the network load evenly. This prevents congestion and ensures faster, more reliable communication.
- Strengthened Network Security: Security is a top priority, and subnetting helps fortify our networks. By isolating devices into separate subnets, we contain potential security breaches. If one subnet is compromised, the rest of the network remains secure.
Understanding IP Addresses
Before diving into subnetting, let’s look at IP addresses. An IP address is a unique identifier assigned to every device connected to a network. It consists of four sets of numbers, separated by periods, such as 192.168.0.1. Each set ranges from 0 to 255, allowing for a total of around 4.3 billion unique IP addresses.
What are Subnet Masks?
Cracking the Code with an Example:
Imagine you’re planning a party, and you want to send invitations only to friends who live in the same city block as you. This is where subnet masks come into play.
1. IP Address and Subnet Mask:
Let’s say your IP address is 192.168.0.100, and your subnet mask is 255.255.255.0. Each number in the subnet mask represents a part of the secret code.
2. The Secret Code Revealed:
In our example, the subnet mask of 255.255.255.0 means that the first three numbers (255.255.255) must match exactly for devices to be in the same subnet. The last number (0) represents the available addresses within the subnet.
3. Party Invitations:
With the subnet mask, you know that all your friends’ IP addresses must have the same first three numbers (192.168.0) to be in your neighborhood. For example, a friend with the IP address 192.168.0.50 would receive an invitation, but someone with the IP address 192.168.1.50 would not, as their first three numbers don’t match.
Check out this informative video on subnet masks to understand how they work: Subnet Masks
Calculating Subnets
To create subnets, we borrow bits from the host portion of the IP address. The number of borrowed bits determines the number of available subnets. For example, by borrowing 3 bits, we can create 2^3 (or 8) subnets.
Host ID, Network ID, and Broadcast ID
In subnetting, we divide the IP address into three parts: the network ID, the host ID, and the broadcast ID. The network ID identifies the specific subnet, the host ID identifies the individual device within that subnet, and the broadcast ID represents the broadcast address for that subnet.
Simple Calculation for Host, Network, and Broadcast ID
In order to compute the network IDs, subnet masks, useable host IDs, broadcast IDs, and host ID ranges for each succeeding subnet using a subnet mask of /28, let’s first discover the first network ID, which is always the original network ID, i.e., 192.168.4.0:
- First Network ID:
- Network ID: 192.168.4.0
- Subnet Mask: /28
- Usable Host IDs: 14 (16 – 2)
- Broadcast ID: 192.168.4.15
- Host ID Range: 192.168.4.1 – 192.168.4.14
- Second Network ID:
- Previous Network ID: 192.168.4.0
- Add 16 (number of hosts) to the previous Network ID: 192.168.4.0 + 16 = 192.168.4.16
- Subnet Mask: /28
- Usable Host IDs: 14 (16 – 2)
- Broadcast ID: 192.168.4.31
- Host ID Range: 192.168.4.17 – 192.168.4.30
- Third Network ID:
- Previous Network ID: 192.168.4.16
- Add 16 (number of hosts) to the previous Network ID: 192.168.4.16 + 16 = 192.168.4.32
- Subnet Mask: /28
- Usable Host IDs: 14 (16 – 2)
- Broadcast ID: 192.168.4.47
- Host ID Range: 192.168.4.33 – 192.168.4.46
- Fourth Network ID:
- Previous Network ID: 192.168.4.32
- Add 16 (number of hosts) to the previous Network ID: 192.168.4.32 + 16 = 192.168.4.48
- Subnet Mask: /28
- Usable Host IDs: 14 (16 – 2)
- Broadcast ID: 192.168.4.63
- Host ID Range: 192.168.4.49 – 192.168.4.62
Explaining the above example
- Usable Host IDs:
- The number of usable host IDs is calculated by subtracting 2 from the total number of hosts in each subnet. The first and last host IDs are reserved for the network ID and broadcast ID, respectively.
- In the given example, the total number of hosts in each subnet is 16.
- Thus, the usable host IDs for each subnet are calculated as 16 – 2 = 14.
- Broadcast IDs:
- The broadcast ID represents the last IP address within a subnet and is used to send a message to all hosts within that subnet.
- To calculate the broadcast ID, we add 1 less than the total number of hosts to the network ID of the subnet.
- In the given example, the total number of hosts in each subnet is 16, so we add 15 (16 – 1) to the network ID.
- The resulting IP address is the broadcast ID for that subnet.
- Host ID Range:
- The host ID range refers to the range of usable IP addresses between the network ID and the broadcast ID in a subnet.
- To calculate the host ID range, we start from the network ID and increment the host ID by 1 until we reach the IP address just before the broadcast ID.
- In the given example, the host ID range can be calculated by starting from the network ID and incrementing the host ID by 1 until we reach the IP address 1 less than the broadcast ID.
You may also like:
https://hackedyou.org/how-does-the-internet-work-simplified/
https://hackedyou.org/tcp-ip-model/
https://hackedyou.org/tcp-ip-vs-osi-model/
https://hackedyou.org/http-status-codes-explained-all/
https://hackedyou.org/what-is-a-cdn-and-how-does-it-work/
https://hackedyou.org/dns-resolver-explained/
https://hackedyou.org/understanding-network-topology/
https://hackedyou.org/10-important-browser-cookies/
https://hackedyou.org/everything-about-internet-cookies/
https://hackedyou.org/network-protocols-types-and-uses/
https://hackedyou.org/hackers-exploiting-open-ports/
https://hackedyou.org/client-server-model/
https://hackedyou.org/ip-addresses-basics-explained/
https://hackedyou.org/top-20-networking-fundamentals-for-hackers/
https://hackedyou.org/artificial-intelligence-transforming-cybersecurity/
https://hackedyou.org/top-10-major-cybersecurity-threats-in-2023/
https://hackedyou.org/mastering-cybersecurity-2023-ultimate-guide/