Networking
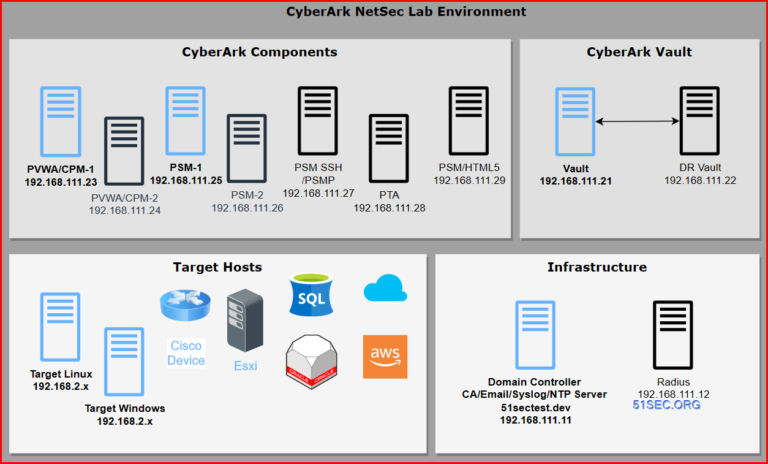
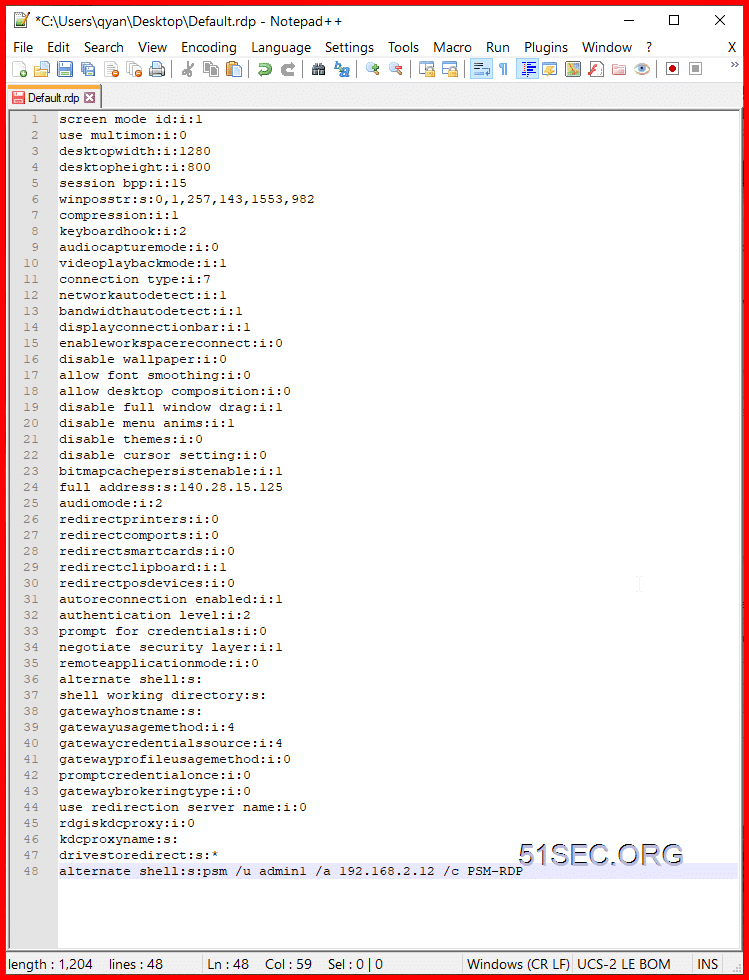
This post is to summarize the steps how to configure a remote connection manager tool to integrate with CyberArk PSM. In this way, you can directly RDP into target server through PSM, without logging...
There are lots of Chinese DOS games in 1980s – 1990s. The Github page (https://github.com/rwv/chinese-dos-games) collected them and created a docker image to simplify the steps to bring them up into...
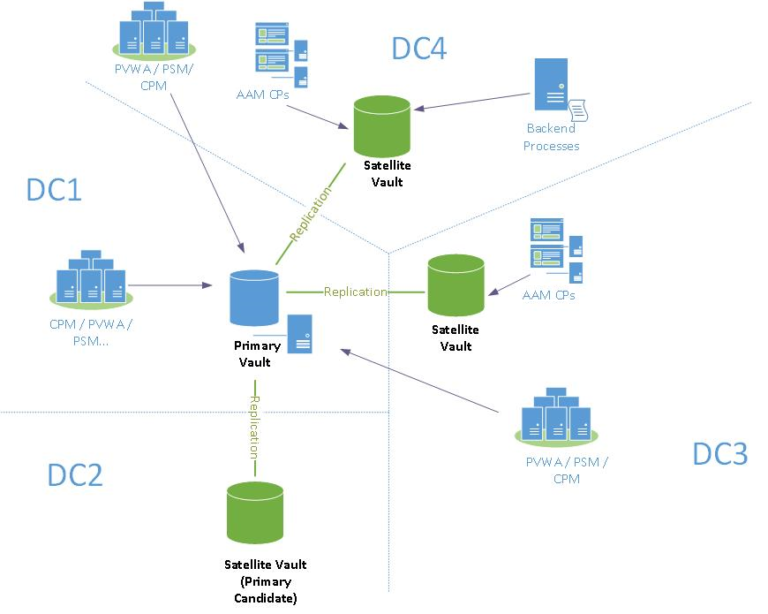
The CPM is installed on a Windows system as an automatic system service called CyberArk Password Manager. It can be stopped and started through the standard Windows service management tools. ...
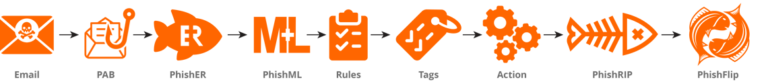
rule Automated_SoftwareEmails { strings: $ = /(n|r)From:.{0,200}.{0,200}</ nocase $ = /(n|r)Subject:.{0,200}/ nocase $ = /(n|r)From:.{0,200}.{0,200}</ nocase $ = /(n|r)Subject:.{0,200}/...
Have you been studying for an AWS certification and have yet to actually test? Now might be the time. AWS is currently offering free retakes of their certification exams. Here are the relevant...
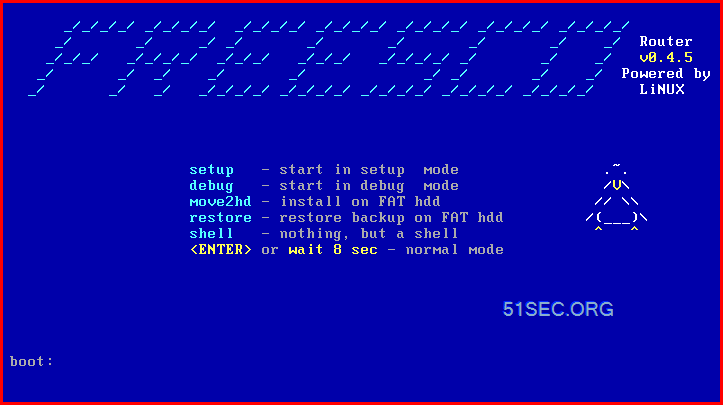
In my home lab virtual environment, VMware ESXi and Workstation used to host most of my testing virtual machines. To get those VMs working together in a multi networks diagram, I always need to have a...
Use Microsoft Entra ID to authorize access to blob data Microsoft Entra ID provides superior security and ease of use over Shared Key for authorizing requests to Blob storage. For more information...
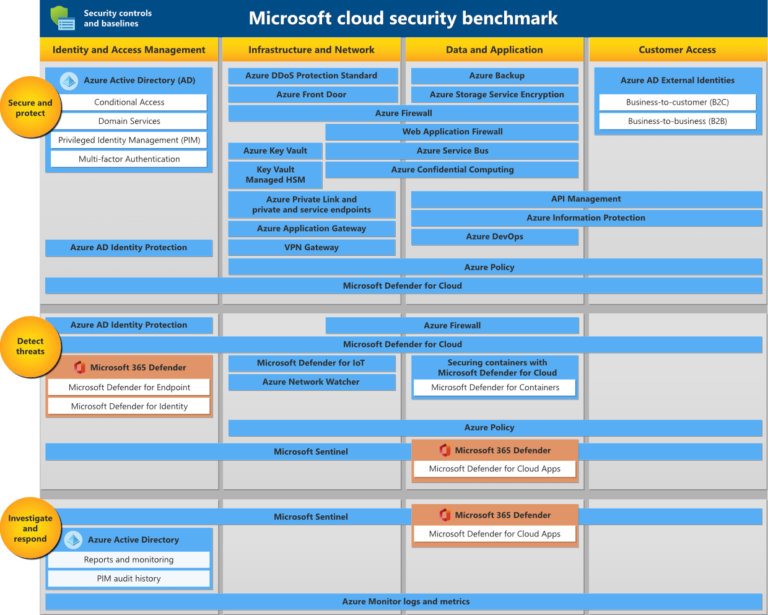
Ensures that the workload meets the uptime and recovery targets by building redundancy and resiliency at scale. Protect the workload from attacks by maintaining confidentiality and data integrity...
This post is just to show some basic Upgrade steps and screenshots for my references. Just fyi, this is only for lab testing, and it is not exactly same as CyberArk Doc suggested. For regular formal...
![[5 Mins Docker] Create Your Own 80s-90s DOS Gaming Website (1898 Games)](https://hackedyou.org/wp-content/uploads/2024/03/5-Mins-Docker-Create-Your-Own-80s-90s-DOS-Gaming-Website-768x516.png)