Introduction:
In today’s interconnected world, network protocols play a crucial role in enabling communication and data transfer across various devices and networks. In this blog, we will explore what network protocols are, their importance, and dive into different types of network protocols along with their common uses. So, let’s get started!
What Are Network Protocols?
Network protocols are a set of rules and guidelines that govern how computers and devices communicate with each other on a network. Think of them as the instructions that enable devices to understand and follow a common language. Just like people need a common language to communicate effectively, devices require protocols to establish reliable communication over a network.
Importance of Network Protocols:
Network protocols are crucial because they ensure that data is transmitted accurately and efficiently between devices. They define how data is formatted, transmitted, received, and interpreted. Without protocols, devices wouldn’t be able to understand each other, resulting in chaos and ineffective communication.
Let’s explore ten important network protocols that you should know:
1. Internet Protocol (IP):
The Internet Protocol, or IP, is like a special language that computers on the Internet use to talk to each other. Just like how people have different addresses to find their homes, IP gives each device on the internet a unique address. This address helps the devices find each other and send information back and forth.
For a more comprehensive understanding of IP addresses and their basics, check out my other blog post on IP addresses explained at https://hackedyou.org/ip-addresses-basics-explained/.
I recommend watching this informative on YouTube https://www.youtube.com/watch?v=ThdO9beHhpA
2. Transmission Control Protocol (TCP):
The Transmission Control Protocol (TCP) is a special set of rules that helps computers communicate with each other over the Internet. It’s like a language that ensures when you send a message or information from your computer to another computer, it arrives safely and in the correct order.
Here’s how it works:
- Imagine you want to send a message to your friend’s computer. TCP takes your message and breaks it into smaller parts called packets. It’s like dividing a big message into smaller pieces, so it’s easier to send.
- TCP attaches some important information to each packet, such as where it’s coming from and where it’s going. This helps the computers know who sent the message and where to send the reply.
- The packets are then sent over the internet, which is like a big network of computers. Sometimes, the packets may take different paths to reach the destination computer.
- When the packets arrive at your friend’s computer, TCP makes sure they are put back together in the right order, just like assembling a puzzle. This way, your friend can read the message exactly as you intended.
- If any packets get lost or damaged along the way, TCP takes care of it. It asks the sender to resend those packets, so nothing important is missing.
I recommend watching this informative on YouTube https://www.youtube.com/watch?v=uwoD5YsGACg
3. Hypertext Transfer Protocol (HTTP):
HTTP (Hypertext Transfer Protocol) is a special set of rules that helps us use the internet and visit websites. It’s like a language that allows our computers to talk to other computers and get information.
Here’s how it works:
- When you type a website address into your browser (like www.example.com), your computer wants to see what’s on that website. So, it sends a message to the server where the website is stored using HTTP.
- The server understands the HTTP message and responds back to your computer. It sends the requested web page or information in a format that your computer can understand.
- Your computer receives the response and displays the web page on your screen. You can see pictures, read text, and interact with the website.
- HTTP also allows you to do things like clicking on links, submitting forms, and downloading files from the internet. When you do any of these actions, your computer sends new HTTP requests to the server, and the server responds with the requested information.
I recommend watching this informative on YouTube https://www.youtube.com/watch?v=hExRDVZHhig
4. File Transfer Protocol (FTP):
FTP (File Transfer Protocol) is a special way for computers to share and exchange files with each other. It’s like a system that helps us transfer files, such as pictures, documents, or videos, from one computer to another.
Here’s how it works:
- Imagine you have a file on your computer that you want to send to your friend’s computer. You use an FTP program or software to connect your computer to your friend’s computer, which is acting as an FTP server.
- Once the connection is established, you can see a list of files and folders on your friend’s computer. It’s like looking at a directory or a menu of options.
- To send a file, you select it from your computer and tell the FTP program to upload it to the server. This means you’re placing the file on your friend’s computer so they can access it.
- The FTP program takes care of the technical details and sends the file over the internet to your friend’s computer. It ensures that the file arrives intact and without errors.
- On your friend’s computer, the FTP program receives the file and saves it in the appropriate location. Now, your friend can access and use the file just like any other file on their computer.
Similarly, if your friend wants to send you a file, they can use FTP to upload it to their server, and you can use an FTP program to download it to your computer.
I recommend watching this informative on YouTube https://www.youtube.com/watch?v=tOj8MSEIbfA
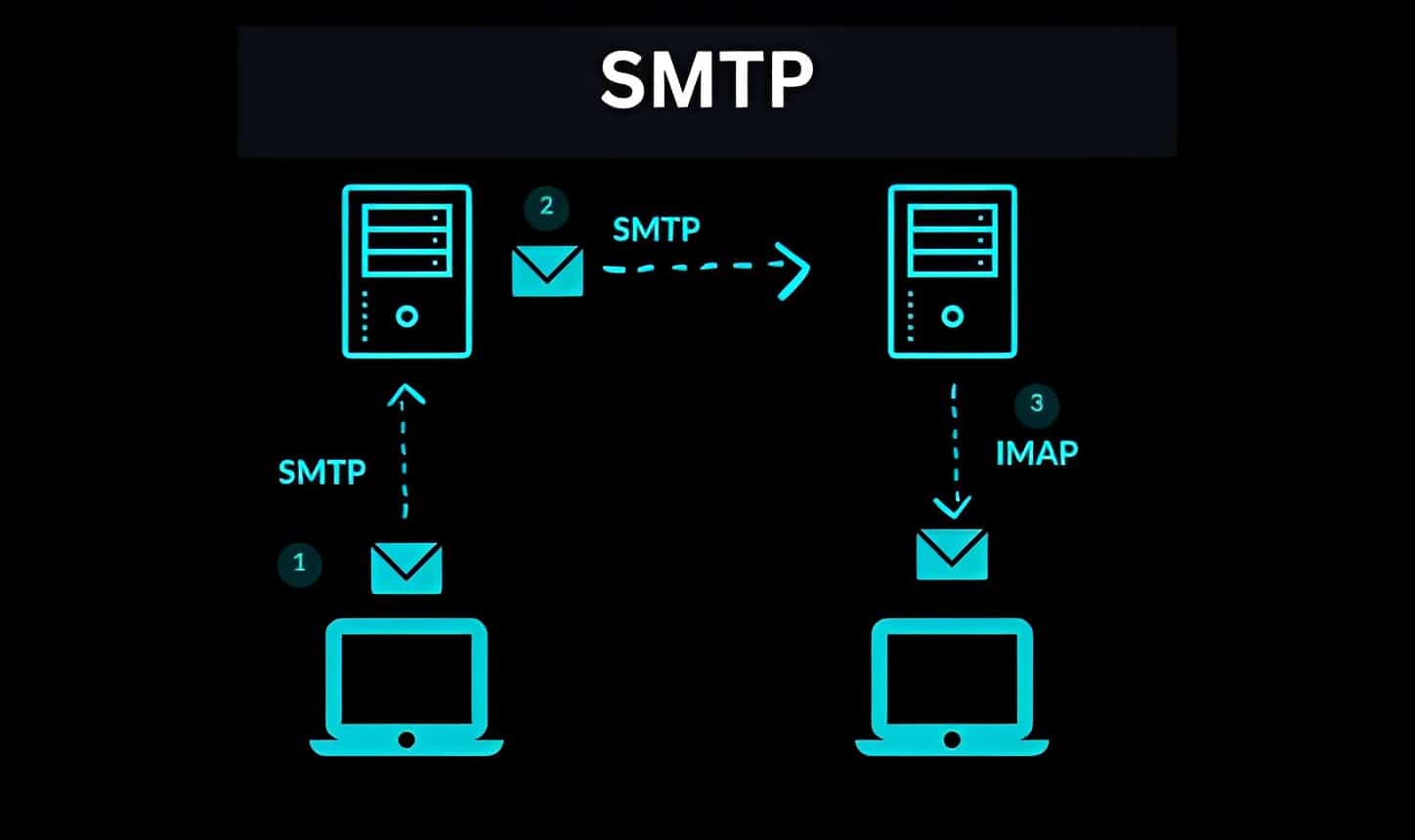
5. Simple Mail Transfer Protocol (SMTP):
SMTP (Simple Mail Transfer Protocol) is like a postman for email. It’s the special language that computers use to send and receive email messages. Its job is to make sure that emails are properly addressed and delivered to the right people.
Here’s how it works:
- When you send an email from your computer, your email program uses SMTP to talk to your email provider’s server. It’s like giving your letter to a postman to send it on your behalf.
- The email server checks the email’s address to make sure it’s going to the right place. It’s like the postman looking at the envelope to see where it needs to be delivered.
- If everything looks good, the server sends the email to the recipient’s email server. It’s like the postman handing off your letter to another postman who can deliver it to the right address.
- The recipient’s email server receives the email and stores it temporarily until the recipient checks their email. It’s like the postman putting the letter in the recipient’s mailbox.
- When the recipient opens their email program, it connects to their email server using SMTP. It’s like the recipient going to their mailbox and picking up the letter.
- The email server sends the email to the recipient’s computer, where it appears in their inbox. It’s like the postman handing the letter directly to the recipient.
I recommend watching this informative on YouTube https://www.youtube.com/watch?v=PJo5yOtu7o8
6. Domain Name System (DNS):
DNS (Domain Name System) is like a phonebook for the internet. It’s a special system that helps your computer find websites by translating human-friendly names (like www.example.com) into computer-friendly addresses called IP addresses. It’s like looking up a contact’s name to find their phone number.
Here’s how it works:
- When you want to visit a website, you type its domain name (like www.example.com) into your web browser.
- Your computer needs to know the IP address of the website to connect to it. IP addresses are like unique phone numbers for computers on the internet.
- Your computer sends a request to a DNS server, asking for the IP address associated with the domain name you entered. It’s like asking a phonebook for the phone number of a person you want to call.
- The DNS server looks up the domain name in its database. It’s like searching the phonebook for the contact’s name.
- Once the DNS server finds the IP address linked to the domain name, it sends it back to your computer.
- Now your computer knows the IP address of the website you want to visit. It can connect directly to that IP address and fetch the web page you requested.
I recommend watching this informative on YouTube https://www.youtube.com/watch?v=mpQZVYPuDGU
7. Internet Message Access Protocol (IMAP):
IMAP (Internet Message Access Protocol) is like a personal mailbox that you can access from anywhere. It’s a special protocol used for managing emails and allows you to access your email messages stored on a mail server from different devices like your computer, smartphone, or tablet. It keeps your emails on the server, so you can view, organize, and manage them from any device.
Here’s how it works:
- When you set up your email account on a device, such as your computer or smartphone, you choose to use IMAP.
- Your device connects to the email server using IMAP. It’s like opening the door to your mailbox.
- Once connected, your device syncs with the mail server and downloads the headers of your email messages. Headers contain information about the emails, like the sender, subject, and date.
- When you open an email or want to view its contents, your device fetches the full email from the server. It’s like opening an envelope to read the letter inside.
- If you read, reply to, or delete an email on one device, the changes are synchronized with the mail server. It’s like making changes to your mailbox that are reflected in the main storage.
- When you access your email from another device, like your smartphone, it connects to the mail server and retrieves the updated information. It’s like accessing the same mailbox from a different location.
- Because your emails are stored on the mail server, you can access them from multiple devices and they stay consistent. If you delete an email on one device, it will also be removed from the server and won’t appear on other devices.
I recommend watching this informative on YouTube https://www.youtube.com/watch?v=SBaARws0hy4
8. Post Office Protocol (POP):
POP (Post Office Protocol) is like collecting all your mail from a post office and taking it home. It’s another email protocol that allows you to download your emails from a mail server to your device. Unlike IMAP, POP typically removes the emails from the server after downloading them to your device.
Here’s how it works:
- When you set up your email account on a device, such as your computer or smartphone, you choose to use POP.
- Your device connects to the mail server using POP. It’s like going to the post office to collect your mail.
- Once connected, your device downloads the email messages from the server to your device. It’s like picking up all the letters and packages from your mailbox at the post office and taking them home.
- The downloaded emails are stored on your device, and you can read, reply to, or organize them offline. It’s like having physical mail in your possession that you can sort and manage at your convenience.
- Unlike IMAP, which keeps your emails on the server, POP usually removes the emails from the server after they are downloaded to your device. It’s like taking the physical mail home with you and leaving an empty mailbox at the post office.
- If you access your email from another device, you won’t see the previously downloaded emails because they are stored only on the device that downloaded them.
- To ensure you have access to your emails from multiple devices, you may need to enable a setting in your POP configuration to leave a copy of the emails on the server for a certain period. This allows you to download the emails to multiple devices before they are removed from the server.
I recommend watching this informative on YouTube https://www.youtube.com/watch?v=SBaARws0hy4
9. Secure Shell (SSH):
SSH (Secure Shell) is like a secret tunnel that keeps your communication safe when you access a computer or server remotely. It provides a secure way to connect to a remote computer over an unsecured network, such as the Internet. It encrypts the data you send and receives, keeping it safe from unauthorized access.
Here’s how it works:
- Let’s say you want to access a computer or server remotely, like controlling your home computer from your laptop while traveling.
- You use an SSH client program on your laptop to establish a connection with the remote computer or server. It’s like creating a secret tunnel between your laptop and the remote computer.
- The SSH client and the remote computer perform a secure handshake. They exchange secret codes to ensure that the connection is trustworthy and encrypted.
- Once the secure connection is established, you can send commands or perform actions on the remote computer through the SSH client. It’s like remotely controlling the computer as if you were sitting in front of it.
- When you type a command or send data from your SSH client, the information is encrypted before being sent over the network. It’s like putting your message in a secret box before sending it through the tunnel.
- The encrypted data travels through the unsecured network, such as the internet, keeping it safe from prying eyes. It’s like your secret box passing through a crowded area without anyone being able to see what’s inside.
- Upon reaching the remote computer, the encrypted data is decrypted and processed. It’s like the secret box being opened and its contents revealed to the remote computer.
- Similarly, when the remote computer sends a response back to your SSH client, the data is encrypted before being transmitted. It ensures that the response remains secure throughout the journey.
- The encrypted communication continues as long as the SSH connection remains active. It keeps your data protected from potential eavesdroppers or unauthorized access.
I recommend watching this informative on YouTube https://www.youtube.com/watch?v=qWKK_PNHnnA
10. Dynamic Host Configuration Protocol (DHCP):
DHCP (Dynamic Host Configuration Protocol) is like a friendly helper that automatically assigns and manages IP addresses for devices on a network. It’s like having someone who takes care of giving each device a special “home address” when they join the network.
Here’s how it works:
- Imagine you have a network with multiple devices, like computers, smartphones, and tablets. Each device needs a unique IP address to communicate on the network. IP addresses are like house addresses for devices on the internet.
- Instead of manually configuring IP addresses for each device, which can be time-consuming and prone to errors, you have DHCP to help you. It’s like having a friendly helper who takes care of assigning addresses automatically.
- When a device connects to the network, it sends a special message called a “DHCP request” to the network’s DHCP server. It’s like the device raising its hand and saying, “Hey, I need an IP address!”
- The DHCP server receives the request and checks its pool of available IP addresses. It picks one that is not currently in use and sends it back to the requesting device. It’s like the helper giving the device a unique address to use.
- The device receives the assigned IP address from the DHCP server and configures itself with that address. It’s like the device putting on a nametag with its new address.
- Now the device can communicate on the network using its assigned IP address. It can send and receive data to other devices and access resources like the internet. It’s like the device having its own special “home address” to be reached by other devices.
- DHCP also sets a lease time for the assigned IP address. After a certain period, the device will contact the DHCP server again to renew its lease or request a new IP address. It ensures that IP addresses are efficiently managed and available for other devices when needed.
- DHCP simplifies network setup and management because you don’t have to manually assign IP addresses to each device. It’s like having a friendly helper take care of the addressing process automatically, saving you time and effort.
I recommend watching this informative on YouTube https://www.youtube.com/watch?v=e6-TaH5bkjo
Conclusion:
Network protocols are the invisible heroes that make our digital world function smoothly. They establish the rules and standards necessary for devices to communicate effectively and ensure the secure and reliable transmission of data. From TCP and IP to HTTP, FTP, and SMTP, each protocol serves a specific purpose, enabling us to browse the internet, transfer files, send emails, and perform numerous other online activities.
You may also like:
Client-Server model – https://hackedyou.org/client-server-model/
Networking Fundamentals – https://hackedyou.org/top-20-networking-fundamentals-for-hackers/
Mastering Cybersecurity – https://hackedyou.org/mastering-cybersecurity-2023-ultimate-guide/
Black hat hacking vs White hat hacking – https://hackedyou.org/hacking-clash-black-hat-white-hat/