What is an IP address?
An IP address, which stands for Internet Protocol address, is a unique numerical label assigned to every device connected to a computer network. It serves as the digital address that identifies and distinguishes each device, allowing them to communicate with each other on the internet. Think of it as a phone number for computers.
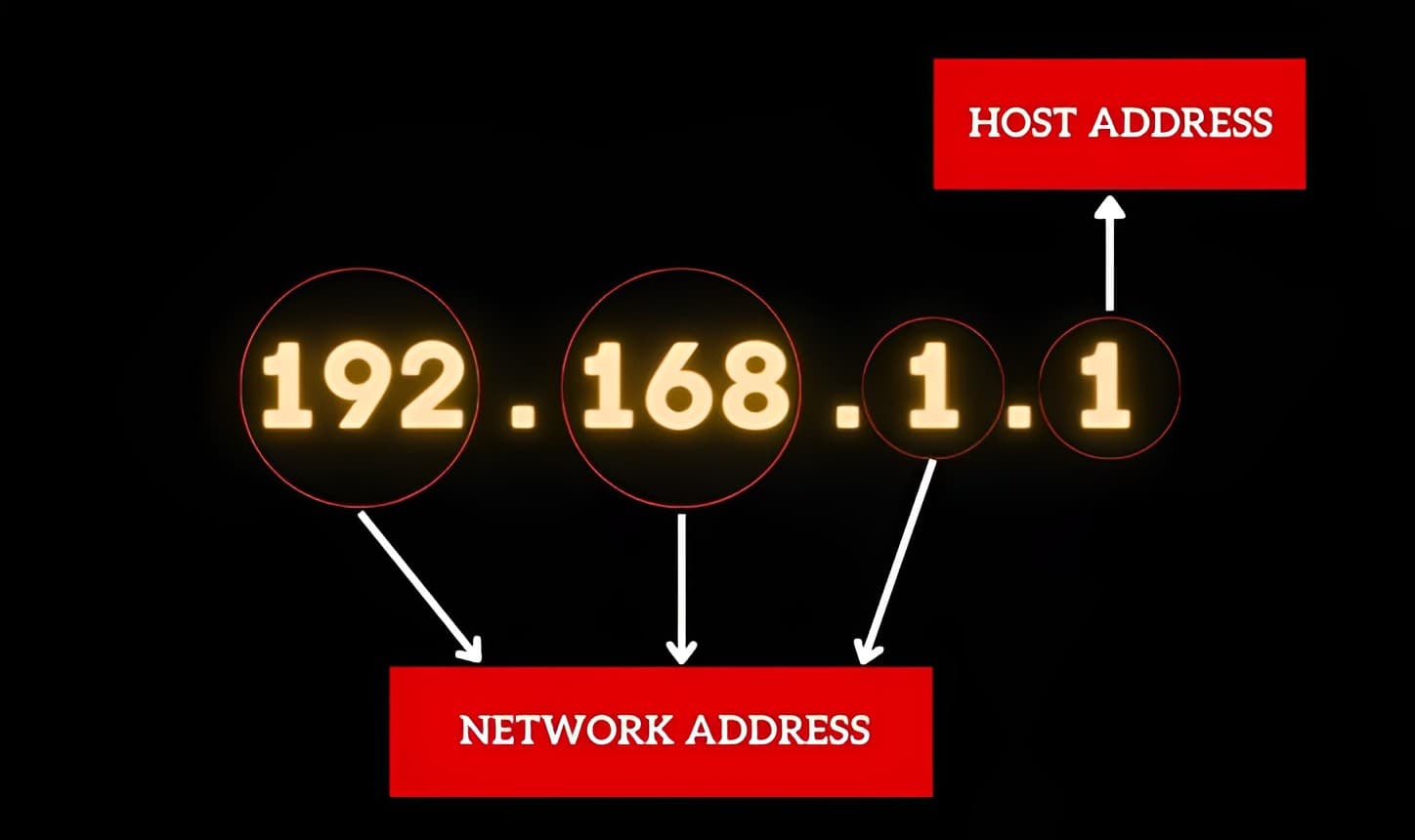
For example, in the address 192.168.1.1, the first three numbers (192.168.1) represent the network, and the last number (1) identifies the specific device. It’s like having a house address (network ID) and a room number (host ID) that help devices find and talk to each other on the internet.
Importance of IP addresses in the digital world
In today’s digital world, IP addresses play a crucial role in enabling communication between devices. Just like how you need someone’s phone number to call them, devices need IP addresses to send and receive information over the internet. Imagine a world without IP addresses – it would be like a giant city without street addresses, where no one could find each other.
How IP addresses enable device communication
IP addresses act as the internet’s bridge, connecting devices worldwide. They help translate human-friendly website addresses into numerical codes, ensuring data packets reach the correct destinations.
By using IP addresses, devices can communicate and exchange information, creating a global network of interconnected devices on the internet. They are the secret code that makes online communication possible.
Types of IP Addresses
IPv4: The traditional IP address format
IPv4 is a common type of IP address used on the internet. It consists of four sets of numbers separated by dots, such as 192.168.1.1.
Structure and components of an IPv4 address
An IPv4 address is made up of four sections, each ranging from 0 to 255. They are separated by dots, and each section represents a unique identifier for a device on a network.
Common IPv4 address ranges and their meanings
Different ranges of IPv4 addresses have specific purposes. For instance, IP addresses starting with 192.168 are often used for private networks, while those starting with 10 are commonly used by large organizations.
IPv6: The future of IP addressing
IPv6 is the next generation of IP addresses. It uses a longer format with eight groups of numbers separated by colons, providing a vast number of addresses for the growing number of devices on the internet.
Key differences between IPv4 and IPv6
IPv6 offers a much larger pool of available addresses compared to IPv4. This allows for better scalability and supports the increasing number of devices connected to the internet.
Advantages and reasons for transitioning to IPv6
Transitioning to IPv6 brings several benefits, including an abundance of IP addresses, improved security features, and better support for emerging technologies. It ensures that all devices can connect and communicate effectively as our digital world continues to expand.
For example, imagine having a small playground with limited space (IPv4) and a massive park with endless room to accommodate more people (IPv6). As our digital population grows, IPv6 provides the necessary space for all devices to connect and thrive.
Embracing IPv6 prepares us for a future where every device, from smartphones to smart homes, can seamlessly connect and make the most of our ever-evolving digital landscape.
How IP Addresses Work
IP address allocation and assignment
IP addresses are essential for devices to communicate on the internet. They are assigned to devices by organizations responsible for managing networks, such as Internet Service Providers (ISPs).
Internet Service Providers (ISPs) and IP address distribution
ISPs play a vital role in distributing IP addresses. They receive a pool of addresses from regional Internet registries and assign them to their customers, like giving unique addresses to different houses in a neighborhood.
Dynamic vs. static IP addresses
There are two types of IP addresses: dynamic and static. Dynamic addresses can change each time a device connects to the internet, while static addresses remain the same. It’s like having a temporary hotel room (dynamic) versus owning a permanent home (static).
Domain Name System (DNS) and IP resolution
The Domain Name System (DNS) acts as a translator between human-friendly domain names, like google.com, and their corresponding IP addresses. It helps devices find the right destination on the internet.
Converting domain names to IP addresses
When you enter a website’s domain name in your browser, your device contacts a DNS server. The DNS server looks up the domain name and returns the IP address associated with it, just like finding an address based on a person’s name.
The role of DNS servers
DNS servers store databases of domain names and their corresponding IP addresses. They facilitate the smooth flow of internet traffic by helping devices locate and connect to the correct IP addresses.
For example, think of a phonebook that helps you find someone’s phone number based on their name. Similarly, DNS servers act as internet phonebooks, translating domain names (like facebook.com) into IP addresses (like 157.240.1.35).
Understanding how IP addresses work, along with the role of DNS servers, ensures devices can find and communicate with each other effectively in the interconnected world of the internet.
IP Address Classes: Understanding Network Address Structure
IP addresses are categorized into different classes (A, B, C, D, and E) to define their range and network structure. These classes provide a framework for organizing and identifying devices on a network. Let’s explore them:
Class A:
Class A addresses are used for large networks. The first octet (the first 8 bits) of a Class A address is dedicated to network identification, while the remaining three octets represent host addresses. For example, an IP address starting with a number between 1 and 126 (e.g., 10.0.0.1) falls into the Class A range.
- Public IP Range: Starts with numbers from 1 to 126, like 10.0.0.0 or 85.123.45.0.
- Private IP Range: Starts with 10.0.0.0 and goes up to 10.255.255.255.
- Subnet Mask: The subnet mask for Class A IP addresses is typically 255.0.0.0. It’s like a special code that helps divide the IP address into two parts: the network portion and the host portion. This allows devices within the same network to communicate with each other.
- Number of Networks: We can create up to 126 different networks using Class A IP addresses.
- Number of Hosts per Network: Each network can have up to 16,777,214 devices connected.
Class B:
Class B addresses are suitable for medium-sized networks. The first two octets are reserved for network identification, and the remaining two octets represent host addresses. IP addresses beginning with numbers between 128 and 191 (e.g., 172.16.0.1) belong to the Class B range.
- Public IP Range: Starts with numbers from 128 to 191, for example, 130.0.0.0 or 185.255.0.0.
- Private IP Range: Starts with 172.16.0.0 and goes up to 172.31.255.255.
- Subnet Mask: The subnet mask for Class B IP addresses is typically 255.255.0.0.
- Number of Networks: We can create around 16,000 different networks using Class B IP addresses.
- Number of Hosts per Network: Each network can have up to 65,000 devices connected.
Class C:
Class C addresses are commonly used for small networks. The first three octets denote network identification, and the last octet represents host addresses. IP addresses starting with numbers between 192 and 223 (e.g., 192.168.0.1) fall into the Class C range.
- Public IP Range: Starts with numbers from 192 to 223, like 200.0.0.0 or 220.255.255.0.
- Private IP Range: Starts with 192.168.0.0 and goes up to 192.168.255.255.
- Special IP Range: Starts with 127.0.0.1 and goes up to 127.255.255.255.
- Subnet Mask: The subnet mask for Class C IP addresses is typically 255.255.255.0.
- Number of Networks: We can create more than 2 million networks using Class C IP addresses.
- Number of Hosts per Network: Each network can have up to 254 devices connected.
Class D:
Class D addresses are specifically designated for multicast purposes. They are used to deliver data to multiple devices simultaneously, forming multicast groups. These addresses range from 224.0.0.0 to 239.255.255.255.
- Public IP Range: Starts with numbers from 224 to 239, like 225.0.0.0 or 238.255.255.255.
- Used for multicasting: Class D IP addresses are used for multicasting, which means sending data to multiple devices simultaneously. Unlike Class A, B, and C, Class D IP addresses do not use subnet masks for dividing into network and host portions.
Class E:
Class E addresses are reserved for experimental or future use and are not utilized for general network addressing.
- Public IP Range: Starts with numbers from 240 to 255, like 241.0.0.0 or 255.255.255.0.
- Reserved for experimental use: Class E IP addresses are reserved for experimental or future use and are not typically used for regular devices. They do not use subnet masks for dividing into network and host portions.
Subnetting: Efficient Network Division
Subnetting involves dividing a network into smaller subnetworks, allowing efficient allocation and management of IP addresses. By subnetting, organizations can create multiple logical networks within a single physical network infrastructure. Let’s understand its importance:
Imagine a large office building with several departments. Each department can be considered a subnet, having its own network. Subnetting helps:
Optimize Address Usage:
Instead of assigning a whole range of IP addresses to a single network, subnetting allows the allocation of smaller address ranges to each subnet. This prevents the wastage of IP addresses and facilitates the growth of the organization.
Improve Network Performance:
By dividing a network into subnets, network traffic can be localized within specific segments. This minimizes unnecessary broadcast traffic and enhances network performance, as communication is limited to relevant subnets.
Enhance Security:
Subnetting enables better security by isolating different segments of a network. Access control lists (ACLs) and firewalls can be implemented to regulate traffic flow between subnets, ensuring data privacy and preventing unauthorized access.
Streamline Network Management:
Subnetting facilitates network organization and management. Administrators can apply specific policies and configurations to individual subnets, assign dedicated resources, and troubleshoot network issues more effectively.
Subnet Mask: Defining Network and Host Portions
A subnet mask accompanies an IP address and helps determine the network and host portions of the address. It consists of a series of 32 bits, with the network portion represented by continuous 1s followed by the host portion represented by continuous 0s.
For instance, a subnet mask of 255.255.255.0 indicates that the first three octets of an IP address represent the network, while the last octet represents the host. Consider the example IP address 192.168.1.100 with the subnet mask 255.255.255.0. Here, the first three octets (192.168.1) identify the network and the remaining octet (100) identifies the host within that network.
Public vs. Private IP Addresses: Discovering Internet Connections
Do you know that devices on the Internet have special addresses, just like houses have addresses? Let’s explore public and private IP addresses and what makes them different:
Public IP Addresses: Unique Internet Identity
A public IP address is like a special code given to devices that connect to the Internet. It helps them talk to other devices all over the world. Just imagine having a phone number that works everywhere.
How Public IP Addresses are Assigned
When you connect to the Internet at home, your Internet Service Provider (ISP) gives your router a public IP address. They make sure each device connected to the Internet gets its own special address. It’s like getting a unique global phone number!
NAT (Network Address Translation): The Connection Helper
Since there are so many devices and not enough public IP addresses, we use Network Address Translation (NAT) to solve the problem. NAT helps devices in local networks talk to the Internet.
To learn more about NAT in detail, you can visit COMPTIA’s NAT blog. They have an informative article that explains what Network Address Translation (NAT) is and how it works. It provides a deeper understanding of NAT and its role in connecting devices on networks. You can find the blog post at the following link: COMPTIA’s NAT Blog
Private IP Addresses: Friends in Your Network
A private IP address is used to talk to other devices in your local network, like your home network. It’s like having special addresses for your family and friends, but they only work inside your house.
Ranges and Usage of Private IP Addresses
Private IP addresses are chosen from special ranges to avoid conflicts with public addresses. The most common private IP ranges are:
Class A: From 10.0.0.0 to 10.255.255.255
Class B: From 172.16.0.0 to 172.31.255.255
Class C: From 192.168.0.0 to 192.168.255.255
So, devices in your home network, like your computer or phone, have private IP addresses that only work inside your house.
NAT and Private IP Address Interaction: The Connection Magic
NAT helps devices with private IP addresses talk to the Internet. When you visit a website, your router with NAT gives your request a temporary public IP address to reach the website. The response from the website is then sent back to your private IP address. It’s like having a translator that helps you understand and talk to the Internet!
With the help of NAT, devices with private IP addresses can access the vast world of the Internet, connecting you to amazing websites, games, and more!
So now you know the secret of public and private IP addresses, where global connectivity meets local networks, making the Internet a wonderful place to explore!
How Hackers Take Advantage of IP Addresses: Revealing Their Tricks
Did you know that hackers can use IP addresses to cause trouble? Let’s uncover how they do it and learn ways to protect ourselves:
Overview of IP Address Vulnerabilities: Weak Spots in the System
IP addresses, help devices communicate over the Internet. However, they also have vulnerabilities that hackers can exploit. These vulnerabilities allow hackers to gain unauthorized access or disrupt network services.
Common Methods Hackers Use to Exploit IP Addresses: Sneaky Tricks
-
IP Spoofing: Impersonating Another IP Address
Imagine someone pretending to be your best friend by using a disguise. That’s what IP spoofing is like for hackers. They pretend to have a different IP address, tricking computers into thinking they are someone else. This allows them to bypass security measures and launch attacks anonymously.
-
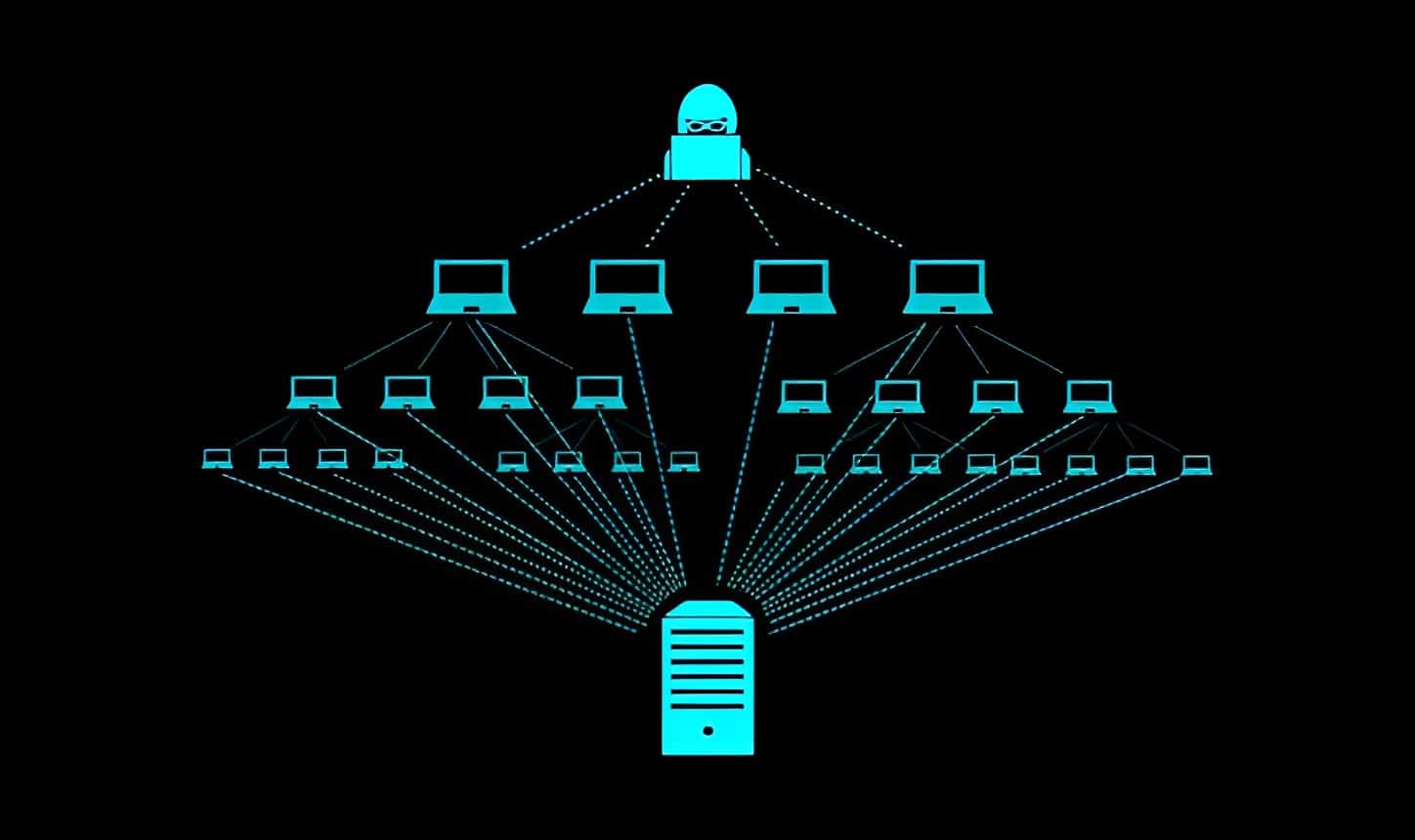
Denial-of-Service (DoS) Attacks: Overwhelming an IP Address
Have you ever seen a traffic jam that stops everything? Well, hackers can create a virtual traffic jam for an IP address. In a DoS attack, they flood the IP address with a massive amount of data or requests, overwhelming it and causing the targeted system to become unresponsive or crash.
To learn more about the potential risks associated with sharing your IP address, visit this informative article on ‘What can someone do with your IP address?
-
IP Scanning and Reconnaissance: Gathering Information for Potential Attacks
Just like spies gather information before a mission, hackers scan IP addresses to gather details about potential targets. They search for weaknesses, such as open ports or outdated software, to plan their next move.
To stay informed about the ever-evolving landscape of cybersecurity threats, be sure to check out our latest blog post. Compiled a comprehensive list of the top 10 major cybersecurity threats in 2023. Visit our blog at https://hackedyou.org/top-10-major-cybersecurity-threats-in-2023/ to gain valuable insights.
Protecting Against IP Address-Based Attacks: Shielding Our Networks
-
Firewalls and Network Security Measures: Digital Shields
Think of firewalls as protective walls around your network. They monitor and filter incoming and outgoing network traffic, blocking malicious connections and allowing only trusted communication.
-
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): Watchful Guardians
IDS and IPS are like vigilant guards that keep an eye on network activities. They analyze traffic, detect suspicious behavior, and take action to prevent potential attacks.
Best Practices for Securing IP Addresses: Locking the Digital Doors
- Keep Software Up to Date: Regularly update your devices and software to fix security vulnerabilities.
- Use Strong Passwords: Create strong, unique passwords for your devices and network to prevent unauthorized access.
- Implement Network Segmentation: Divide your network into smaller segments, making it harder for hackers to access critical systems.
IP Geolocation and How It’s Used
Understanding IP Geolocation
IP geolocation helps us find out where a computer or device is located using its unique IP address. An IP address is like an online address for a device, and by looking at it, we can get an idea of where that device is in the world.
What is IP Geolocation Used For?
1. Targeted Advertising
Companies can use IP geolocation to show ads to people based on where they are. For example, if you’re in New York, you might see ads for local businesses or events happening nearby. This makes the ads more relevant to you and increases the chances of you being interested in them.
Example: Let’s say you’re looking at a website, and you live in San Francisco. The website uses IP geolocation to show you ads for a nearby restaurant, promoting their daily specials and inviting you to visit them.
2. Content Localization
IP geolocation helps websites provide content in your preferred language and show prices in your local currency. It makes the website more user-friendly and useful for people from different countries.
Example: Imagine you’re shopping online, and the website knows you’re from Germany based on your IP address. It automatically translates the website into German, shows prices in Euros, and offers shipping options specific to Germany. This makes it easier for you to shop and understand everything.
3. Fraud Prevention
IP geolocation is also used to keep us safe online. By checking the IP address, websites and banks can detect if someone is trying to do something bad or illegal. For example, if someone tries to access your bank account from a different country, the bank can recognize this and take extra steps to protect your account.
Example: If a bank sees that someone is trying to log into your account from a different country, they might temporarily lock the account and ask you if it’s really you. This helps stop potential fraudsters from stealing your money or personal information.
The Future of IP Addresses
Have you ever wondered what the future holds for IP addresses? Let’s dive into the exciting world of tomorrow and discover the possibilities that await us:
IPv4 Exhaustion and the Transition to IPv6: Finding a Solution
Imagine if there were only a limited number of phone numbers available for the whole world. That’s what’s happening with IPv4 addresses, the ones we currently use. They’re running out because more and more devices are connecting to the Internet. But fear not, a new solution called IPv6 is here to save the day!
IPv6 introduces a much larger pool of IP addresses. It’s like having billions and billions of phone numbers available for all the devices in the world. This means we can connect even more gadgets and appliances to the Internet without running out of addresses. It’s an upgrade that ensures everyone gets their own unique address.
Internet of Things (IoT) and IP Addressing Challenges: A Connected World
Imagine a future where everyday objects like your watch, refrigerator, and even your shoes are connected to the Internet. They can talk to each other and make your life easier. This interconnected web of devices is called the Internet of Things (IoT). But connecting so many devices comes with its own set of challenges, especially when it comes to IP addressing.
With the IoT, we’ll need a lot more IP addresses to assign to all these smart devices. IPv6 steps in again, providing a massive pool of addresses to accommodate the growing number of connected devices. Now, each device can have its very own unique address, enabling seamless communication and functionality.
Emerging Technologies and Their Impact on IP Addressing: Embracing the Future
The future is filled with exciting technologies that will shape the world of IP addressing. Let’s explore a few of them:
- 5G Networks: The next generation of mobile networks promises lightning-fast speeds and the ability to connect many more devices at once. This means we’ll need a robust IP addressing system to handle the increased demand for connections.
- Artificial Intelligence (AI): AI is changing the way we do things, from voice assistants to self-driving cars. In the world of IP addressing, AI can help optimize how addresses are assigned and managed, making the process more efficient.
- Edge Computing: Edge computing brings the power of processing closer to devices, reducing delays and improving performance. This might require innovative IP addressing techniques to effectively manage the network architecture.
As we continue to push the boundaries of technology, IP addressing will evolve alongside it, adapting to meet the demands of our connected world.
Understanding the Risks Associated with IP Addresses and the Importance of Security Measures:
- The Dark Side of the Internet: Cyber Threats: Unfortunately, not everyone on the Internet has good intentions. Some people try to harm or steal information from others. IP addresses can sometimes be targeted by hackers to gain unauthorized access to our devices and personal data.
- Guarding Your Digital Fortress: Security Measures: To protect ourselves from cyber threats, we need to set up virtual fortresses around our devices. These fortresses include things like firewalls, antivirus software, and strong passwords. They keep the bad guys out and ensure our digital safety.