The purpose of the CyberArk Dashboard entry is to provide Remote Desktop Manager users with an interface that eliminates the need to use Password Vault Web Access (PVWA) to see the list of safes and credentials that the currently logged on user has access to. Combined with password-less scenarios and/or our rich role-based access control (RBAC), this means that a user does NOT need to know the CyberArk credentials to be presented with a list of accounts they have access to. Additionally, since the dashboard is meant to authenticate once to your server and, most importantly, maintain an active session for as long as it is active, it has the significant advantage of only requiring MFA once when you launch the dashboard.
Another design principle of the dashboard is that its main usage model is to go through the CyberArk Privileged Session Manager (PSM) to reach assets. This means that Remote Desktop Manager does NOT need to read the password for the account to be used. Less secure models are available to support older scenarios that some of our customers are still using.
How it is working
How it is working for Devolutions RDM integrating with CyberArk PAM solution:
Below is an example diagram demonstrating how Remote Desktop Manager integrates with CyberArk’s PAM Solution

- The end-user attempts to access a privileged remote connection through RDM.
- RDM confirms that the end user’s certificate is valid.
- RDM connects to CyberArk and requests the necessary credentials.
- CyberArk accepts the request and sends the credentials to RDM.
- The credentials are used to grant the end-user access, so they can complete their work-related task.
At no point in this process does the end-user see the credentials!
Basic Devolutions RDM Operation
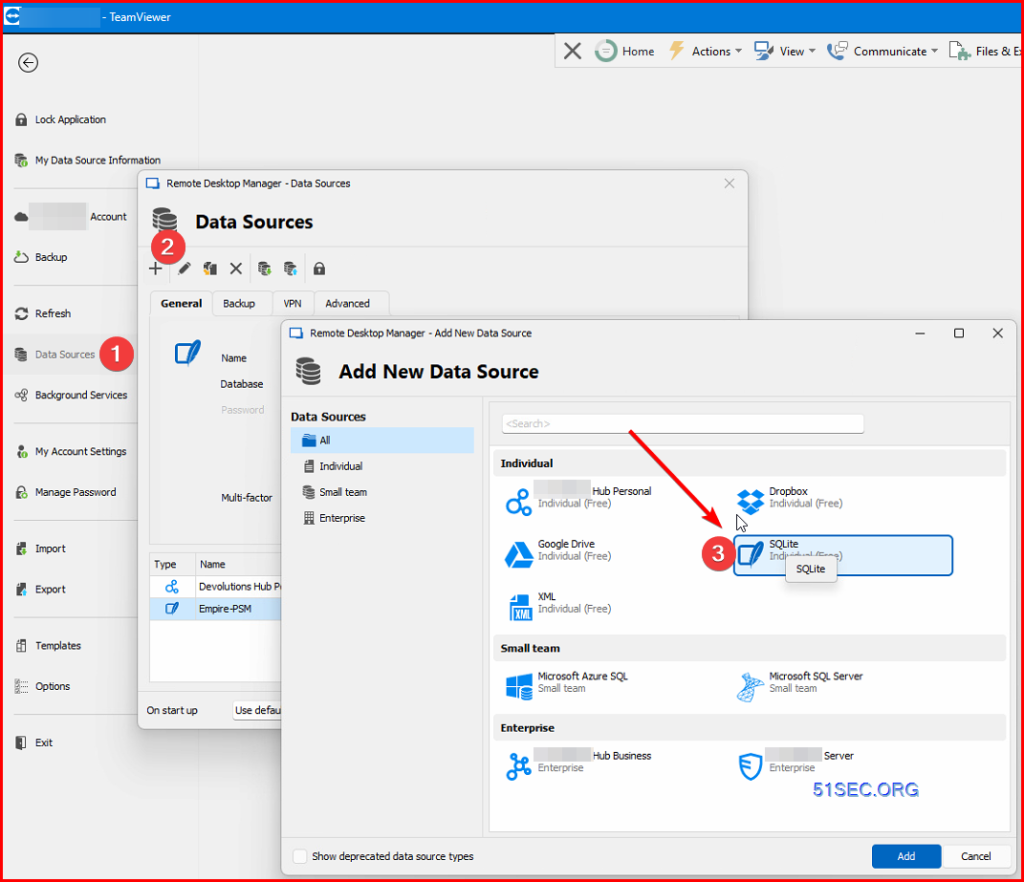
1. Add new data source
SQLite is local light DB usually for personal usage.
SQLite db will be saved to folder at C:\Users\Netsec\Appdata\Local\Devolutions\RemoteDesktopManager
2. Add License
This is to use PSM /u /a /c string to create a session using PSM to connect to remote.
Devolutions RDM CyberArk Dashboard
Once you added the license, the hidden entey template for CyberArk will be available.
1. Select CyberArk Template
Session templates – CyberArk Dashboard
Credential Mgmt Template
2. Use CyberArk Dashboard Template
Enter https://51sec.cyberark.cloud/privilegecloud as Web Services URL.
Choose SAML as authentication mode
for self-hosted environment:
virtual directory will need to have / at the front
3. Advanced Settings
Override screen size for better embedding experience
No need to use PSM as connection
Synchronizer
Create a new entry for Synchronizer
GitHub Project for PSM Template
Steps
- Install RDM from Devolutions
- Start RDM and log in (either with a free account or an enterprise account)
- Import the template from this repo
- Create a folder if you want to group connections
- Add entry -> Add from template
- Select the template you imported in step 3 and replace information thats within brackets <>, including the brackets
The target account is defined as username@address, where the fields corrosponds with the fields in CyberArk.
New Template / Import Template
PSM-SSH or Other Remote APP
To get PSM-SSH session embedded into RDM Client, you will need to DisableRemoteApp function for the connector. Else, you will have to use “Open external” session.