As more organizations move to hardware tokens and password-less auth (e.g. Yubi-keys, Windows Hello for Business,…) attackers will look for other ways to to trick users to gain access to their data.
One novel phishing technique is by using the OAuth2 Device Authorization Grant.
This post describes how it works with Microsoft AAD as example.
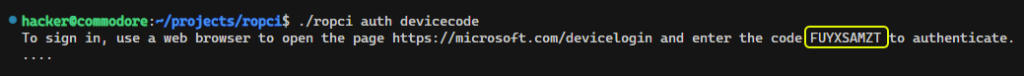
The attacker starts a Device Code flow by issuing a request to the device code token endpoint (e.g. https://login.microsoftonline.com/{tenant}.onmicrosoft.com/oauth2/v2.0/devicecode).
ropci has this feature built in, but it can be issued with curl or Burp.
./ropci auth devicecode
The command returns the URL and a Code to complete the authorization.
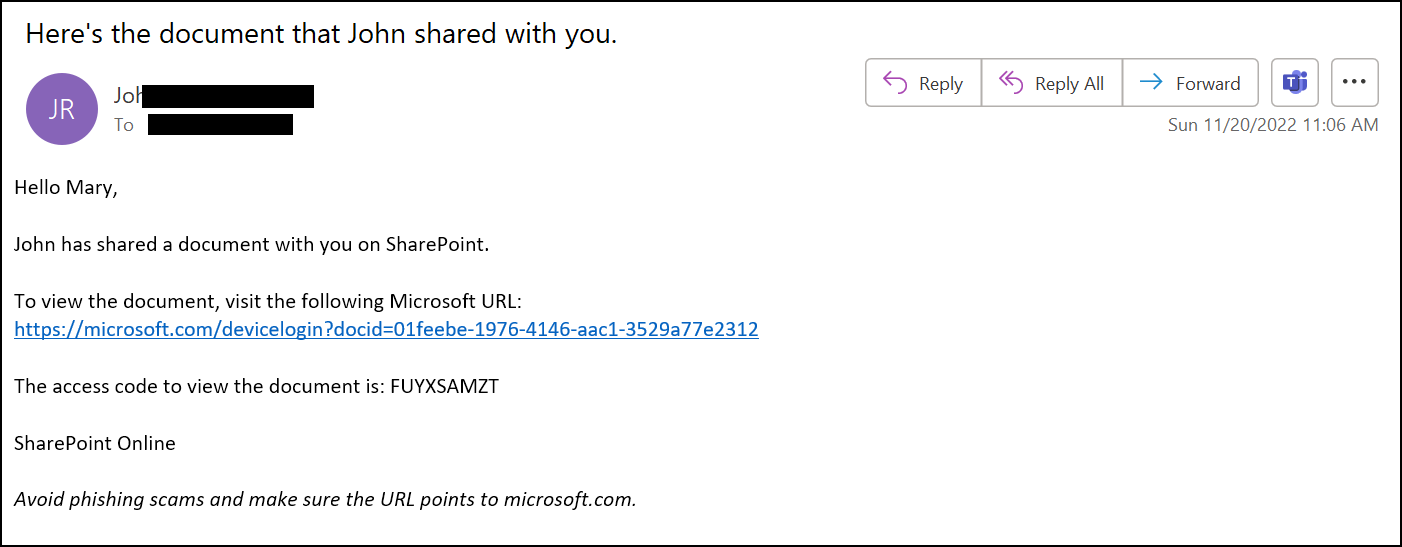
Attacker sends the phishing email to the victim
The attacker grabs the Code puts it into a phishing email:
To make the phish more realistic, one can add additional query parameters, like a docid above.
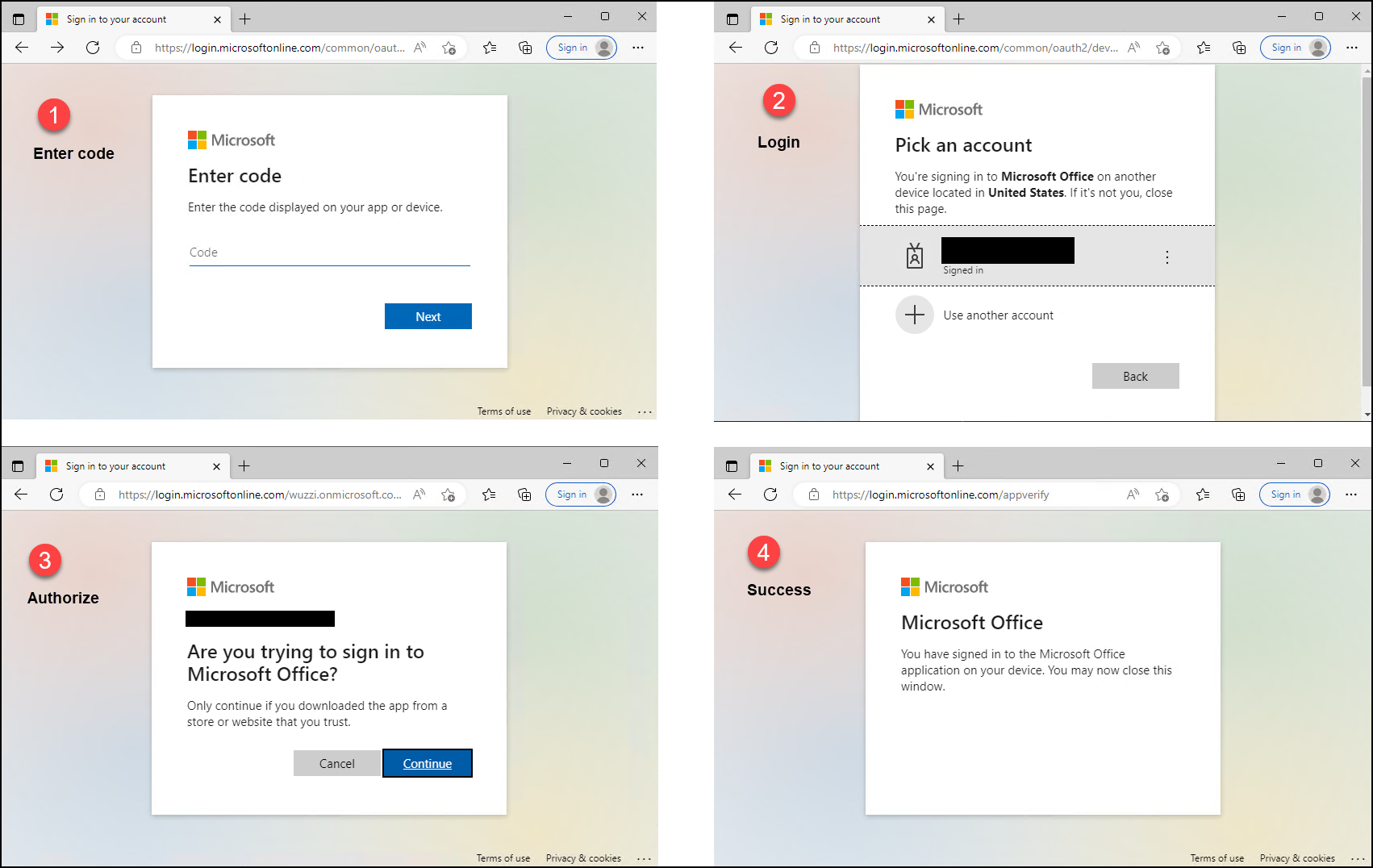
Victim falls for the phish
There are a couple of steps the victim has to complete in order to grant authorization:
The above images shows the individual steps:
- Click the link in the email and enter the device code
- Login to Microsoft Online (in many cases the user might already be logged in)
- Authorize the OAuth app (in this example Office, which is the default client_id ropci uses)
- Success
Completing these steps is necessary before an access token will be issued.
Attack receives the access token
Once the victim completes the OAuth flow and grants access, the attacker receives the access token!
The attacker can now use ropci to read the users email, search mail/SharePoint, send mail, read info from all users/groups/apps/devices in the AAD tenant, basically anything that Microsoft Graph API allows.
There is typically a short time window while the device code is valid, which the attacker has to leverage. This means attack campaigns will be automated at scale to increase chances of success (requesting of token and automatic sending of mails).
- The easiest is likely to entirely disable the Device Code flow in your organization, unless there is a true business need to support it.
- Keeping the time window short to limit an attacker’s chance
- Reviewing and monitoring the device code flow initiator and the host that grants access. Both of these hosts/devices should likely be coming from a similiar IP address.