CyberArk Vendor Privileged Access Manager (Vendor PAM) is an integrated SaaS solution that enables fast and secure privileged access for vendors, consultants, maintenance personnel and other authorized external 3rd parties. With Vendor PAM, organizations can implement Zero Trust-based just-in-time access, biometric MFA, and privileged credential and session management without the need for VPN clients, passwords, and agents. Vendor PAM helps defend against attacks targeting 3rd-party access, while driving operational efficiencies and satisfying audit and compliance requirements.
Diagram
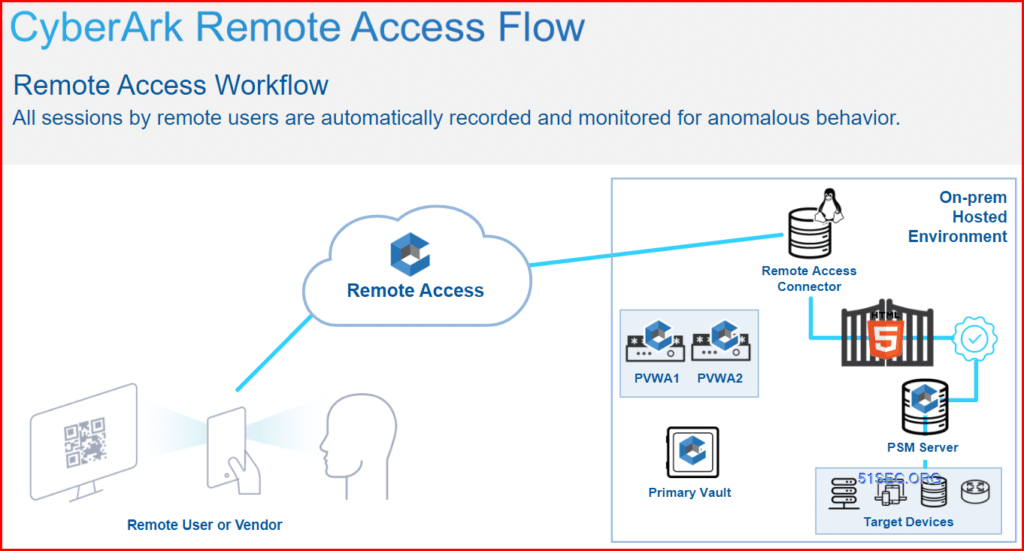
When a remote user attempts to log in to the CyberArk web portal, Remote Access displays a one-time, short-lived QR code on the users’s workstation. Using the CyberArk Mobile app, the user scans the QR code and simultaneously authenticates their identity by means of facial or fingerprint recognition. If both the QR code and the biometric data are approved, the remote user is granted secure access to the CyberArk web portal and authorized to access privileged accounts from their workstation. The web browser session is isolated, and credentials are never shared to the end user’s workstation when they enter into critical IT systems for regular work, maintenance, or otherwise. The session is encrypted end-to-end.
1 Invite vendor to CyberArk PAS
Make sure the identity role for the new vendor account has access Remote Access user portal.
2 Vendor will need to install CyberArk Mobile and register CyberArk Remote Access App
You will need a cell phone number which has never registered into your CyberArk cloud subscription before.
3 Vendor received invite then click Join URL
Use CyberArk Mobile App sign into to remote access portal and complete the invitation
4 Vendor will only able to see allowed Applications
After vendor clicked the application, such as VendorPAM, the vendor will only be able to see the allowed accounts from VendorPAM.
5 Vendor’s account will also need to be activated by Remote Access admin
6 Make sure you have this new account has reader role to the safe in Privilege Cloud.
You will need onboard certain privilege account into the safe then provide account read permission to this safe, which is basic configuration in the Privilege cloud.
Troubleshooting
1. Access Denied
It usually happens when admin testing an account. Open a new incognito browser and type https://portal.alero.io