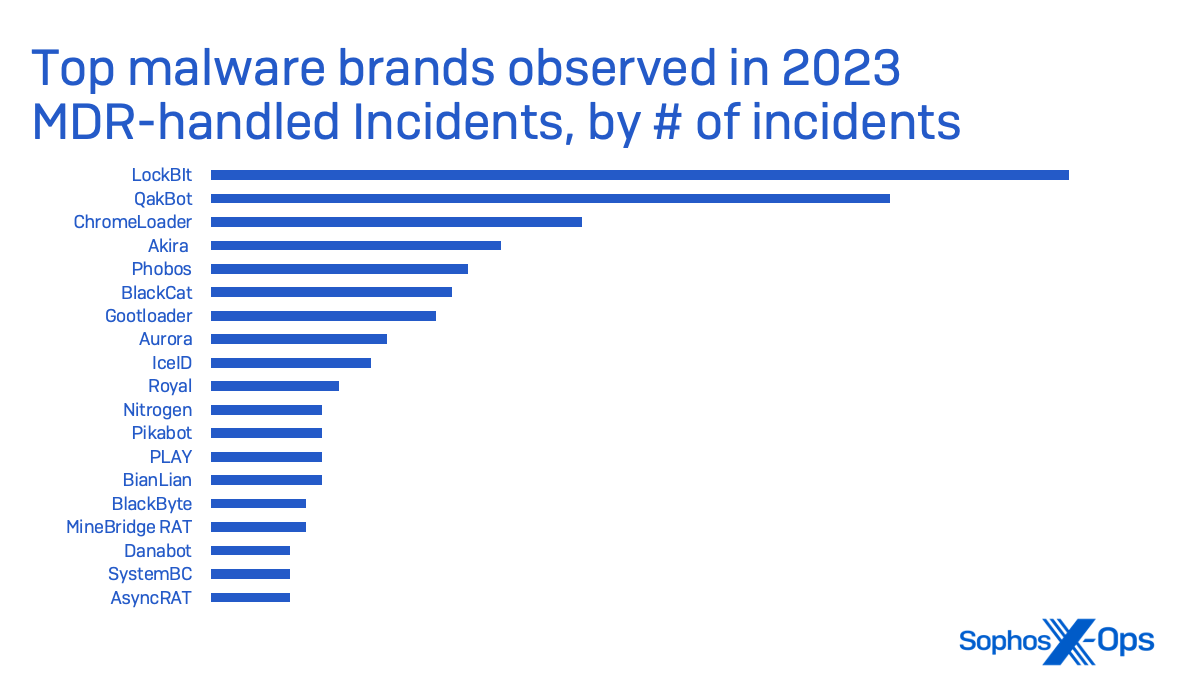
59 CVEs primed for Microsoft’s March Patch Tuesday
On Tuesday Microsoft released 59 CVEs, including 41 for Windows. A remarkable 20 other product groups or tools are also affected. Of the CVEs addressed, just two are considered Critical in severity by Microsoft, both in Windows (specifically, in Hyper-V).
At patch time, none of the issues has been publicly disclosed, or is known to be under active exploit in the wild. Six of the important-severity vulnerabilities in Windows are by the company’s estimation more likely to be exploited in the next 30 days. Five of the issues addressed are amenable to detection by Sophos protections, and we include information on those in a table below.
In addition to these patches the release included advisory information on four patches related to the Edge browser; three of those CVEs were assigned by the Chrome team, not Microsoft. (More on Microsoft’s Edge patch, CVE-2024-26167, in a minute.) There is also one Important-severity issue, CVE-2023-28746, for which advisory information is given this month.
We don’t include advisories in the CVE counts and graphics below, but we provide information on all of them in an appendix at the end of the article. We are as usual including at the end of this post three other appendices listing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product family.
By the Numbers
- Total Microsoft CVEs (excluding Edge): 59
- Total Edge / Chrome issues covered in update: 4
- Total non-Microsoft CVEs covered in update: 1
- Publicly disclosed: 0
- Exploited: 0
- Severity
- Critical: 2
- Important: 57
-
- Elevation of Privilege: 25
- Remote Code Execution: 18
- Denial of Service: 6
- Information Disclosure: 5
- Security Feature Bypass: 2
- Spoofing: 2
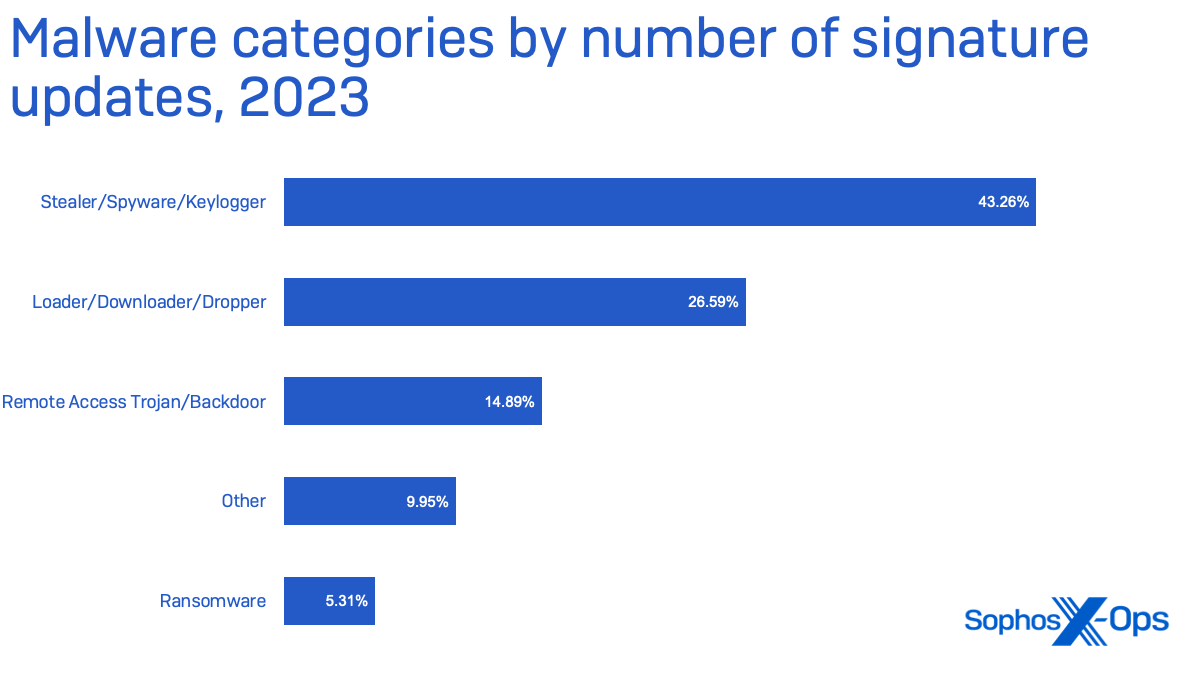
- Tampering: 1
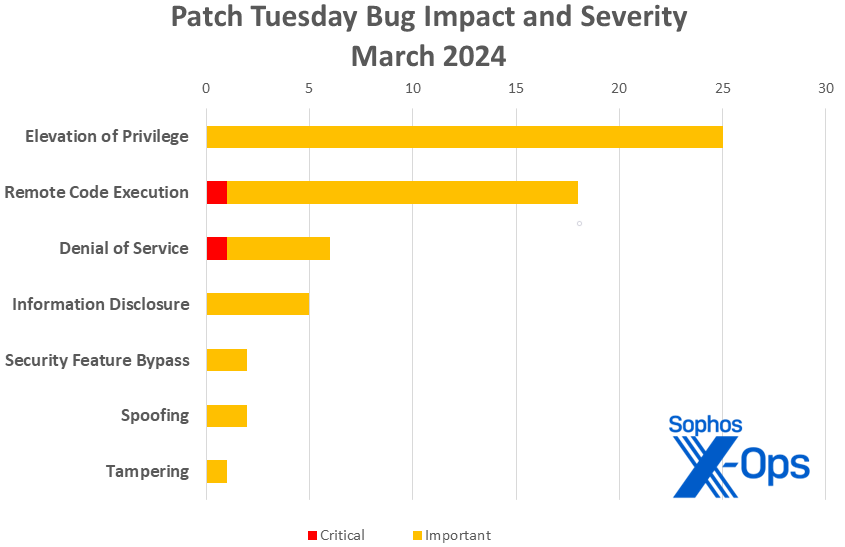
Figure 1: And just like that, 2024 ties 2023’s entire output of tampering CVEs… at one. More on CVE-2024-26185 in a minute
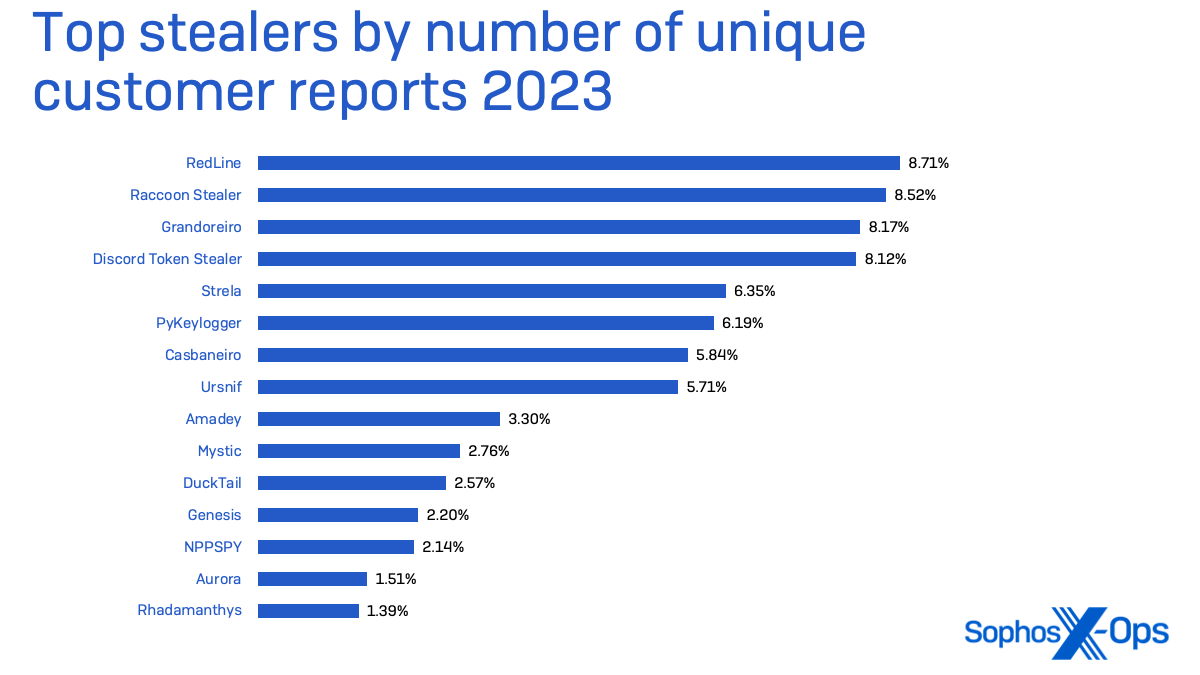
Products
- Windows: 41 (including one shared with .NET and Visual Studio)
- Azure: 4 (including one shared with Log Analytics Agent, OMI, OMS, and SCOM)
- Visual Studio: 3 (including one shared with .NET and one shared with .NET and Windows)
- .NET: 2 (including one shared with Visual Studio and one shared with Visual Studio and Windows)
- OMI (Open Management Infrastructure): 2 (including one shared with Azure, Log Analytics Agent, OMS, and SCOM; and one shared with SCOM)
- SCOM (System Center Operations Manager): 2 (including one shared with Azure, Log Analytics Agent, OMI, and OMS; and one shared with OMI
- Authenticator: 1
- Defender: 1
- Dynamics 365: 1
- Exchange: 1
- Intune: 1
- Log Analytics Agent: 1 (shared with Azure, OMI, OMS, and SCOM)
- Office (365 on-premises): 1
- OMS (Operations Management Suite Agent for Linux): 1 (shared with Azure, OMI, and SCOM)
- Outlook: 1
- SharePoint: 1
- Skype: 1
- SONiC (Software for Open Networking in the Cloud): 1
- SQL: 1
- Teams: 1
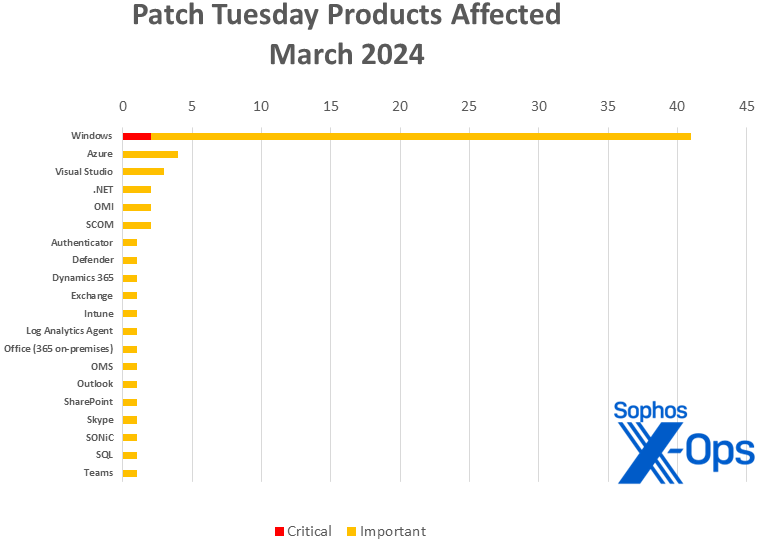
Figure 2: There’s something for everyone, as twenty tools or product groups are touched by the March Patch Tuesday angel
Notable March updates
In addition to the issues discussed above, a few specific items merit attention.
CVE-2024-26185
Windows Compressed Folder Tampering Vulnerability
One of the six issues Microsoft believes more likely to be exploited in the next 30 days, this vulnerability affects the ubiquitous 7zip. Minimal user interaction is required, most likely via email (in which the attacker sends a specially crafted file and convinces the user to open it) or via the web. This patch applies only to Win11 22H2 and Win11 23H2.
CVE-2024-21334
Open Management Infrastructure (OMI) Remote Code Execution Vulnerability
Sporting the month’s highest CVSS score (9.8 base) and yet not likely to be exploited in the next 30 as judged by Microsoft, this RCE applies to not just OMI but to SCOM (System Center Operations Manager) 2019 and 2022 as well. If exploited, a unauthenticated remote attacker could access the OMI instance via the internet and send specially crafted requests to trigger a use-after-free vulnerability. (If patching’s not an immediate option, Linux machines that don’t need network listening can disable their incoming OMI ports by way of mitigation.)
CVE-2024-21421
Azure SDK Spoofing Vulnerability
Check the date of your last deployment: Was it prior to October 19, 2023? If so, you’ll need to manually update to Azure Core Build 1.29.5 or higher. (For convenience, Azure SDK’s GitHub is available here.) Those with deployments after that date already received the fix automatically.
CVE-2024-21448
Microsoft Teams for Android Information Disclosure
There are a number of Android-related patches this month – Intune, Outlook, the Edge patch we’ll discuss below – but only this one, an important-severity Teams issue, will require a trip to the Play Store. Exploitation would allow the attacker to read files from the private directory of the application.
CVE-2024-26167
Microsoft Edge for Android Spoofing Vulnerability
As an Edge vulnerability, this one arrives with scant information from Microsoft, which in the post-IE era mainly takes its browser updates outside the Patch Tuesday cycle. As an Android vulnerability, it may well be that Android users will take this update from other sources. What’s clear from Microsoft is that whatever it is and whoever’s patching it, the patch is not yet available, and that those concerned should keep an eye on the publicly posted CVE information for updates. Fortunately, with a 4.3 CVSS base score, this mystery may well be a tempest in a teapot.
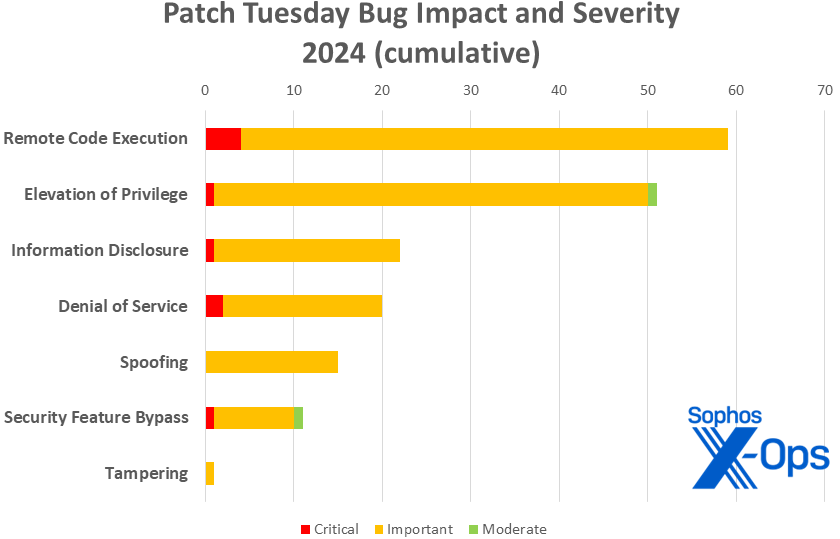
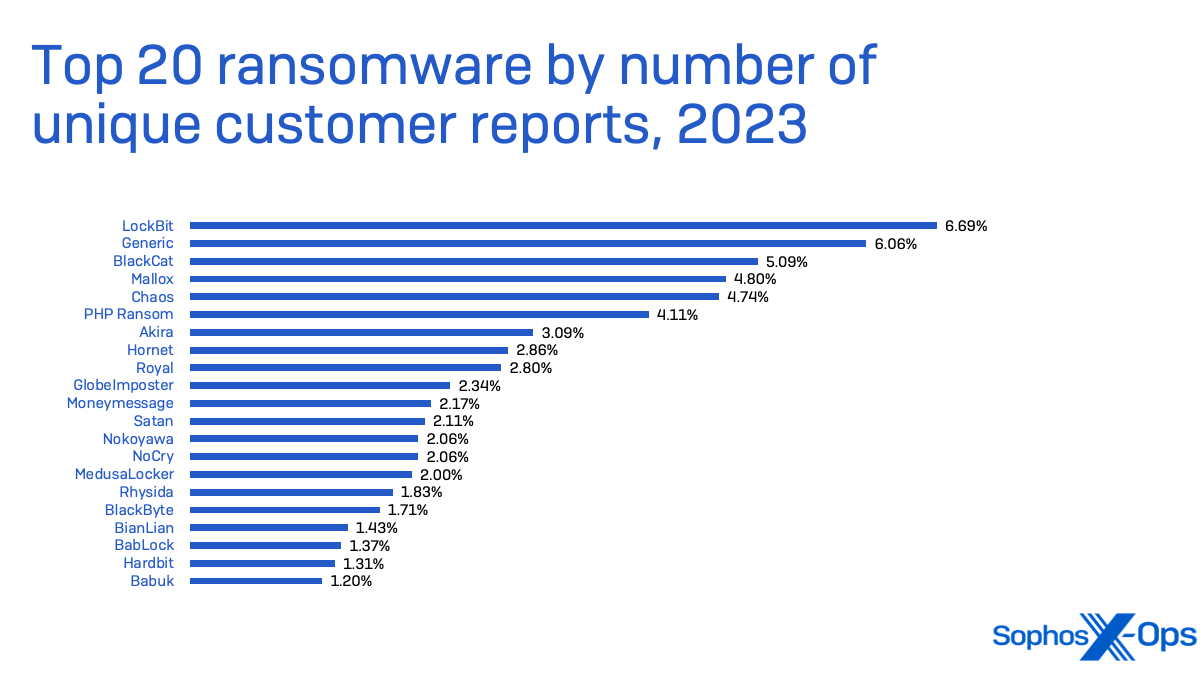
Figure 3: March continues the trend so far in 2024 of lighter-than-usual patch loads. So far in 2024 there have been 179 patches released in the normal second-Tuesday cadence, compared with 246 in 2023, 225 in 2022, 228 in 2021, and 266 in 2020
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-21433 | Exp/2421433-A | Exp/2421433-A |
| CVE-2024-21437 | Exp/2421437-A | Exp/2421437-A |
| CVE-2024-26160 | Exp/2426160-A | Exp/2426160-A |
| CVE-2024-26170 | Exp/2426170-A | Exp/2426170-A |
| CVE-2024-26182 | Exp/2426182-A | Exp/2426182-A |
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of March patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Elevation of Privilege (25 CVEs)
| Important severity | |
| CVE-2024-21330 | Open Management Infrastructure (OMI) Elevation of Privilege Vulnerability |
| CVE-2024-21390 | Microsoft Authenticator Elevation of Privilege Vulnerability |
| CVE-2024-21400 | Microsoft Azure Kubernetes Service Confidential Container Elevation of Privilege Vulnerability |
| CVE-2024-21418 | Software for Open Networking in the Cloud (SONiC) Elevation of Privilege Vulnerability |
| CVE-2024-21431 | Hypervisor-Protected Code Integrity (HVCI) Security Feature Bypass Vulnerability |
| CVE-2024-21432 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-21433 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2024-21434 | Microsoft Windows SCSI Class System File Elevation of Privilege Vulnerability |
| CVE-2024-21436 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2024-21437 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-21439 | Windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-21442 | Windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2024-21443 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21445 | Windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2024-21446 | NTFS Elevation of Privilege Vulnerability |
| CVE-2024-26165 | Visual Studio Code Elevation of Privilege Vulnerability |
| CVE-2024-26169 | Windows Error Reporting Service Elevation of Privilege Vulnerability |
| CVE-2024-26170 | Windows Composite Image File System (CimFS) Elevation of Privilege Vulnerability |
| CVE-2024-26173 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26176 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26178 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26182 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26199 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2024-26201 | Microsoft Intune Linux Agent Elevation of Privilege Vulnerability |
| CVE-2024-26203 | Azure Data Studio Elevation of Privilege Vulnerability |
Remote Code Execution (18 CVEs)
| Critical severity | |
| CVE-2024-21407 | Windows Hyper-V Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-21334 | Open Management Infrastructure (OMI) Remote Code Execution Vulnerability |
| CVE-2024-21411 | Skype for Consumer Remote Code Execution Vulnerability |
| CVE-2024-21426 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2024-21429 | Windows USB Hub Driver Remote Code Execution Vulnerability |
| CVE-2024-21430 | Windows USB Attached SCSI (UAS) Protocol Remote Code Execution Vulnerability |
| CVE-2024-21435 | Windows OLE Remote Code Execution Vulnerability |
| CVE-2024-21440 | Microsoft ODBC Driver Remote Code Execution Vulnerability |
| CVE-2024-21441 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-21444 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-21450 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-21451 | Microsoft ODBC Driver Remote Code Execution Vulnerability |
| CVE-2024-26159 | Microsoft ODBC Driver Remote Code Execution Vulnerability |
| CVE-2024-26161 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-26162 | Microsoft ODBC Driver Remote Code Execution Vulnerability |
| CVE-2024-26164 | Microsoft Django Backend for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-26166 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-26198 | Microsoft Exchange Server Remote Code Execution Vulnerability |
Denial of Service (6 CVEs)
| Critical severity | |
| CVE-2024-21408 | Windows Hyper-V Denial of Service Vulnerability |
| Important severity | |
| CVE-2024-21392 | .NET and Visual Studio Denial of Service Vulnerability |
| CVE-2024-21438 | Microsoft AllJoyn API Denial of Service Vulnerability |
| CVE-2024-26181 | Windows Kernel Denial of Service Vulnerability |
| CVE-2024-26190 | Microsoft QUIC Denial of Service Vulnerability |
| CVE-2024-26197 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
information Disclosure (5 CVEs)
| Important severity | |
| CVE-2024-21448 | Microsoft Teams for Android Information Disclosure |
| CVE-2024-26160 | Windows Cloud Files Mini Filter Driver Information Disclosure Vulnerability |
| CVE-2024-26174 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2024-26177 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2024-26204 | Outlook for Android Information Disclosure Vulnerability |
Security Feature Bypass (2 CVEs)
| Important severity | |
| CVE-2024-20671 | Microsoft Defender Security Feature Bypass Vulnerability |
| CVE-2024-21427 | Windows Kerberos Security Feature Bypass Vulnerability |
Spoofing (2 CVEs)
| Important severity | |
| CVE-2024-21419 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
| CVE-2024-21421 | Azure SDK Spoofing Vulnerability |
Tampering (1 CVE)
| Important severity | |
| CVE-2024-26185 | Windows Compressed Folder Tampering Vulnerability |
Appendix B: Exploitability
This is a list of the March CVEs judged by Microsoft to be more likely to be exploited in the wild within the first 30 days post-release. The list is arranged by CVE.
| Exploitation more likely within the next 30 days | |
| CVE-2024-21433 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2024-21437 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-26160 | Windows Cloud Files Mini Filter Driver Information Disclosure Vulnerability |
| CVE-2024-26170 | Windows Composite Image File System (CimFS) Elevation of Privilege Vulnerability |
| CVE-2024-26182 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26185 | Windows Compressed Folder Tampering Vulnerability |
Appendix C: Products Affected
This is a list of March’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family.
Windows (41 CVEs)
| Critical severity | |
| CVE-2024-21407 | Windows Hyper-V Remote Code Execution Vulnerability |
| CVE-2024-21408 | Windows Hyper-V Denial of Service Vulnerability |
| Important severity | |
| CVE-2024-21427 | Windows Kerberos Security Feature Bypass Vulnerability |
| CVE-2024-21429 | Windows USB Hub Driver Remote Code Execution Vulnerability |
| CVE-2024-21430 | Windows USB Attached SCSI (UAS) Protocol Remote Code Execution Vulnerability |
| CVE-2024-21431 | Hypervisor-Protected Code Integrity (HVCI) Security Feature Bypass Vulnerability |
| CVE-2024-21432 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-21433 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2024-21434 | Microsoft Windows SCSI Class System File Elevation of Privilege Vulnerability |
| CVE-2024-21435 | Windows OLE Remote Code Execution Vulnerability |
| CVE-2024-21436 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2024-21437 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2024-21438 | Microsoft AllJoyn API Denial of Service Vulnerability |
| CVE-2024-21439 | Windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-21440 | Microsoft ODBC Driver Remote Code Execution Vulnerability |
| CVE-2024-21441 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-21442 | Windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2024-21443 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21444 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-21445 | Windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2024-21446 | NTFS Elevation of Privilege Vulnerability |
| CVE-2024-21450 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-21451 | Microsoft ODBC Driver Remote Code Execution Vulnerability |
| CVE-2024-26159 | Microsoft ODBC Driver Remote Code Execution Vulnerability |
| CVE-2024-26160 | Windows Cloud Files Mini Filter Driver Information Disclosure Vulnerability |
| CVE-2024-26161 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-26162 | Microsoft ODBC Driver Remote Code Execution Vulnerability |
| CVE-2024-26166 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-26169 | Windows Error Reporting Service Elevation of Privilege Vulnerability |
| CVE-2024-26170 | Windows Composite Image File System (CimFS) Elevation of Privilege Vulnerability |
| CVE-2024-26173 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26174 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2024-26176 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26177 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2024-26178 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26181 | Windows Kernel Denial of Service Vulnerability |
| CVE-2024-26182 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26185 | Windows Compressed Folder Tampering Vulnerability |
| CVE-2024-26190 | Microsoft QUIC Denial of Service Vulnerability |
| CVE-2024-26197 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
Azure (4 CVEs)
| Important severity | |
| CVE-2024-21330 | Open Management Infrastructure (OMI) Elevation of Privilege Vulnerability |
| CVE-2024-21400 | Microsoft Azure Kubernetes Service Confidential Container Elevation of Privilege Vulnerability |
| CVE-2024-21421 | Azure SDK Spoofing Vulnerability |
| CVE-2024-26203 | Azure Data Studio Elevation of Privilege Vulnerability |
Visual Studio (3 CVEs)
| Important severity | |
| CVE-2024-21392 | .NET and Visual Studio Denial of Service Vulnerability |
| CVE-2024-26165 | Visual Studio Code Elevation of Privilege Vulnerability |
| CVE-2024-26190 | Microsoft QUIC Denial of Service Vulnerability |
.NET (2 CVEs)
| Important severity | |
| CVE-2024-21392 | .NET and Visual Studio Denial of Service Vulnerability |
| CVE-2024-26190 | Microsoft QUIC Denial of Service Vulnerability |
OMI (2 CVEs)
| Important severity | |
| CVE-2024-21330 | Open Management Infrastructure (OMI) Elevation of Privilege Vulnerability |
| CVE-2024-21334 | Open Management Infrastructure (OMI) Remote Code Execution Vulnerability |
SCOM (2 CVEs)
| Important severity | |
| CVE-2024-21330 | Open Management Infrastructure (OMI) Elevation of Privilege Vulnerability |
| CVE-2024-21334 | Open Management Infrastructure (OMI) Remote Code Execution Vulnerability |
Authenticator (1 CVE)
| Important severity | |
| CVE-2024-21390 | Microsoft Authenticator Elevation of Privilege Vulnerability |
Defender (1 CVE)
| Important severity | |
| CVE-2024-20671 | Microsoft Defender Security Feature Bypass Vulnerability |
Dynamics 365 (1 CVE)
| Important severity | |
| CVE-2024-21419 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
Exchange (1 CVE)
| Important severity | |
| CVE-2024-26198 | Microsoft Exchange Server Remote Code Execution Vulnerability |
Intune (1 CVE)
| Important severity | |
| CVE-2024-26201 | Microsoft Intune Linux Agent Elevation of Privilege Vulnerability |
Law Analytics Agent (1 CVE)
| Important severity | |
| CVE-2024-21330 | Open Management Infrastructure (OMI) Elevation of Privilege Vulnerability |
Office (1 CVE)
| Important severity | |
| CVE-2024-26199 | Microsoft Office Elevation of Privilege Vulnerability |
OMS (1 CVE)
| Important severity | |
| CVE-2024-21330 | Open Management Infrastructure (OMI) Elevation of Privilege Vulnerability |
Outlook (1 CVE)
| Important severity | |
| CVE-2024-26204 | Outlook for Android Information Disclosure Vulnerability |
SharePoint (1 CVE)
| Important severity | |
| CVE-2024-21426 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
Skype (1 CVE)
| Important severity | |
| CVE-2024-21411 | Skype for Consumer Remote Code Execution Vulnerability |
SONiC (1 CVE)
| Important severity | |
| CVE-2024-21418 | Software for Open Networking in the Cloud (SONiC) Elevation of Privilege Vulnerability |
SQL (1 CVE)
| Important severity | |
| CVE-2024-26164 | Microsoft Django Backend for SQL Server Remote Code Execution Vulnerability |
Teams for Android (1 CVE)
| Important severity | |
| CVE-2024-21448 | Microsoft Teams for Android Information Disclosure |
Appendix D: Advisories and Other Products
This is a list of advisories and information on other relevant CVEs in the March Microsoft release, sorted by product.
Relevant to Edge / Chromium (4 CVEs)
| CVE-2024-2173 | Chromium: CVE-2024-2173 Out of bounds memory access in V8 |
| CVE-2024-2174 | Chromium: CVE-2024-2174 Inappropriate implementation in V8 |
| CVE-2024-2176 | Chromium: CVE-2024-2176 Use after free in FedCM |
| CVE-2024-26167 | Microsoft Edge for Android Spoofing Vulnerability |
Relevant to Windows (non-Microsoft release) (one CVE)
| CVE-2023-28746 | Intel: CVE-2023-28746 Register File Data Sampling (RFDS) |
59 CVEs primed for Microsoft’s March Patch Tuesday Read More »